WebStrike Lab
Reviewed PCAP for Webshell Upload Attack.

Link
Process
Oh no! Looks like our server got hit with a web shell in WebStrike Lab. Let’s dive in and see what happened.
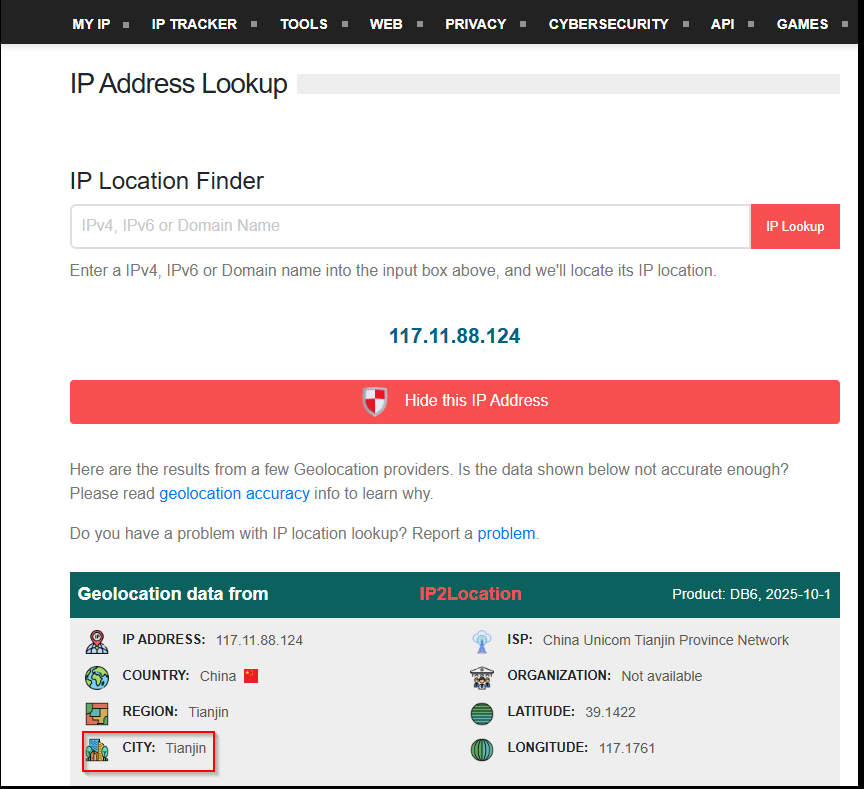
First up, let’s identify the IP of the attacker from the PCAP in WireShark.

Next, we can geolocate where the attack originated from based on that IP.
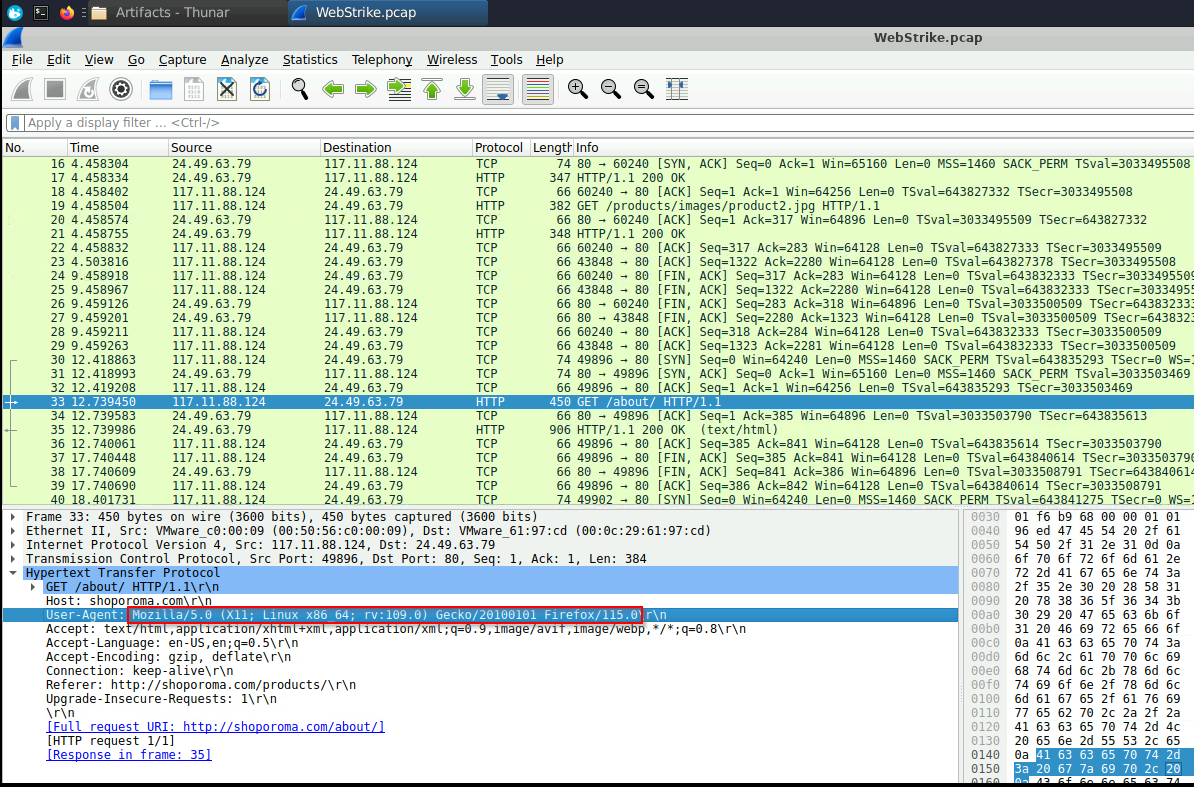
From the same request, we can identify the attacker’s User-Agent.
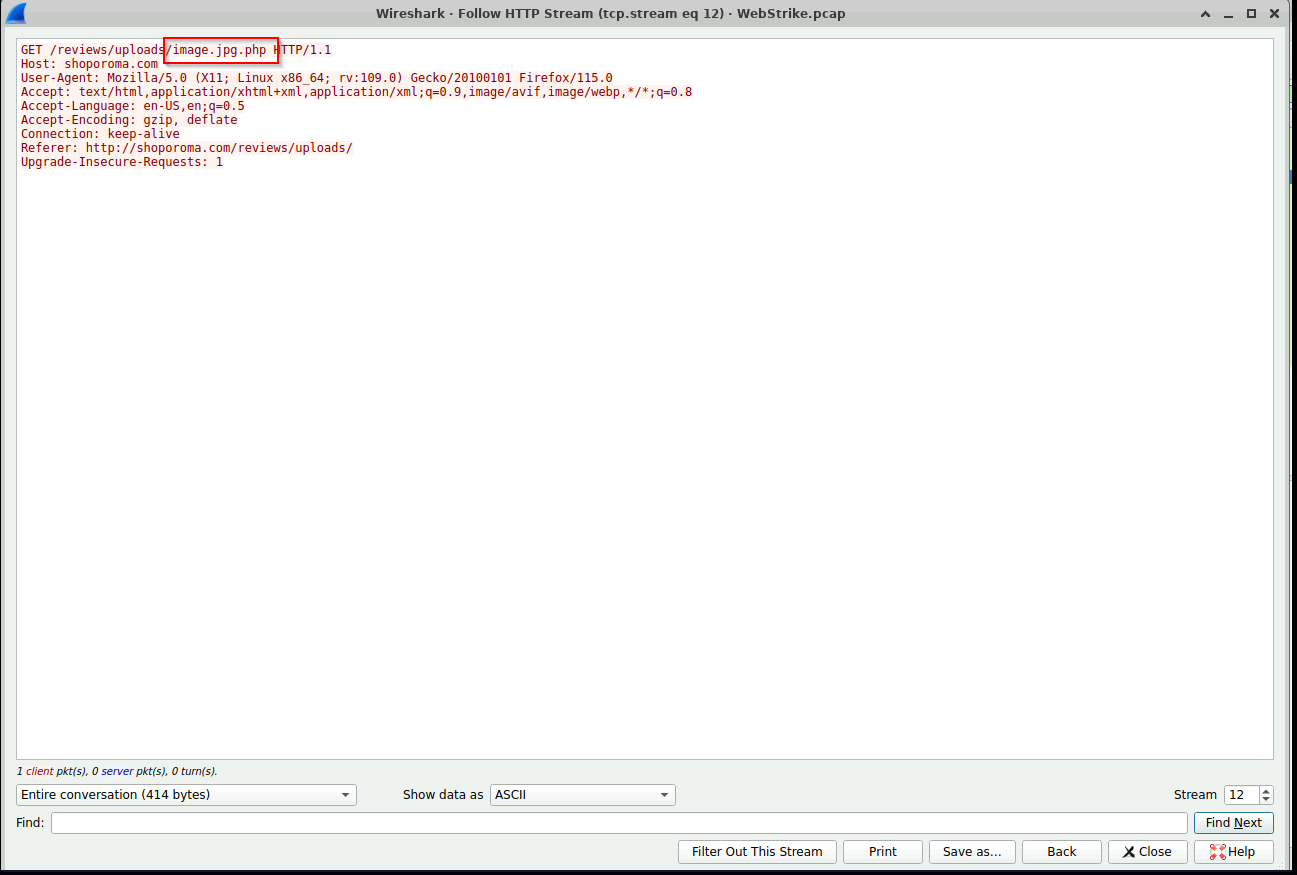
It is also really important to find the name of the malicious shell. We can get this from the GET request they used to trigger it.
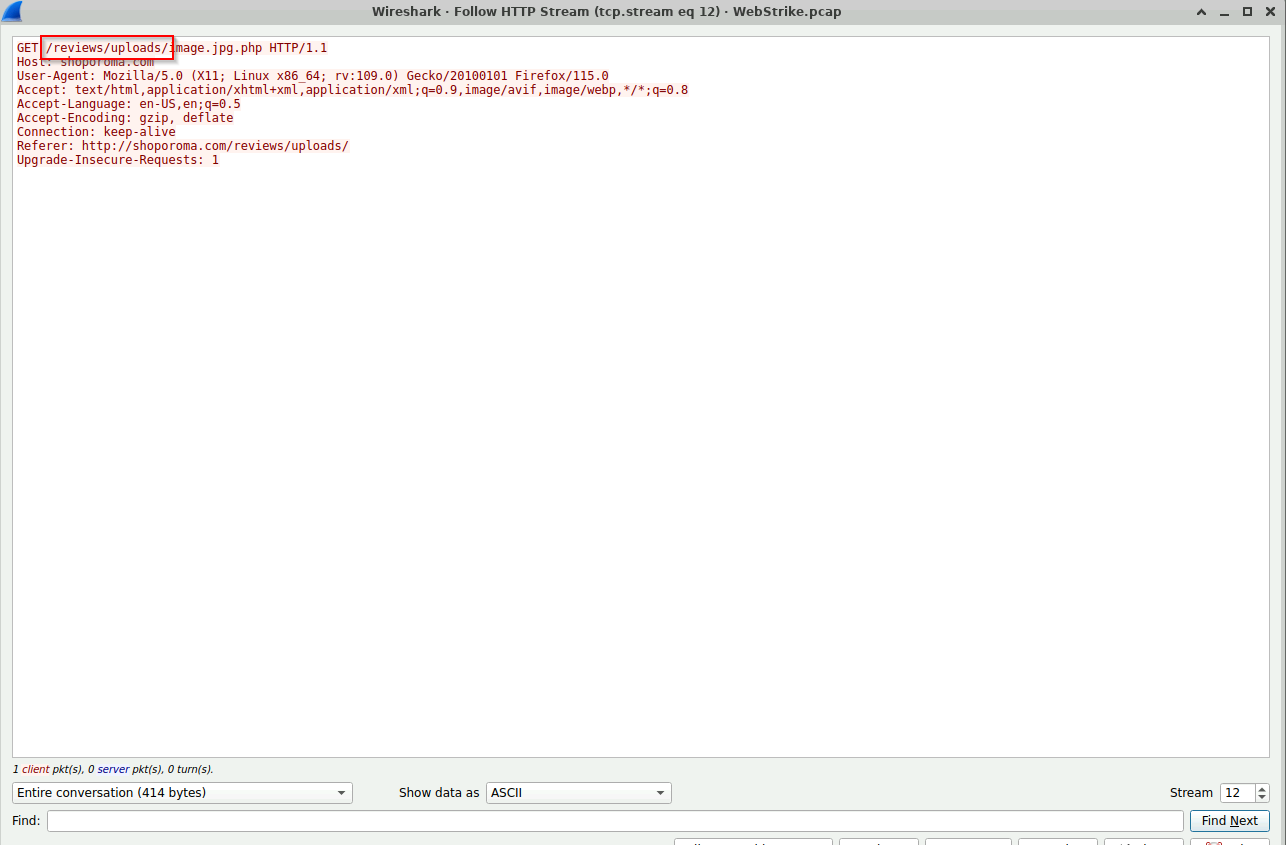
From this same request, we can also identify the folder that the file was uploaded to.
Shortly after that GET request, the connection is made and we can get the local port, or LPORT, the attacker was using.
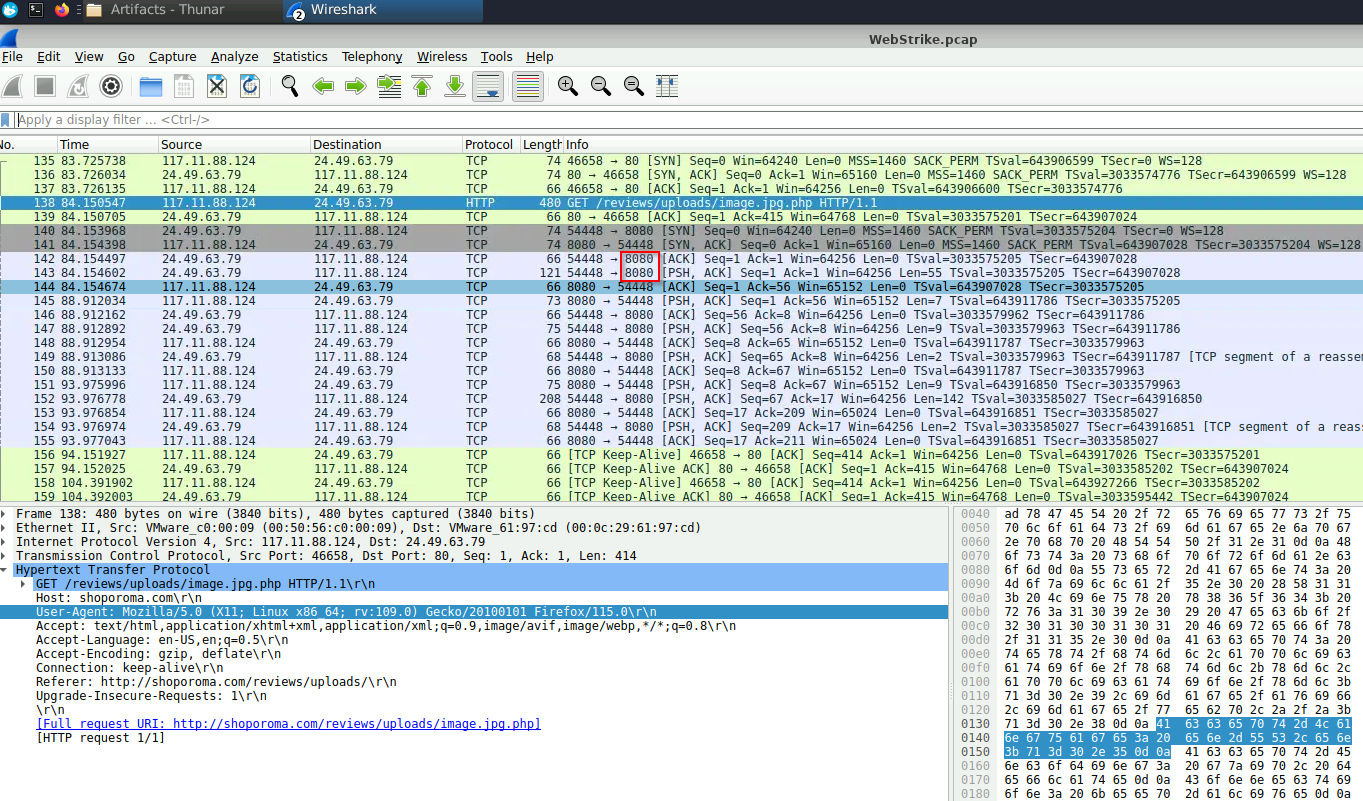
Finally, we need to know what data was exfiltrated. We can do this by following the TCP Stream and giving it a peek.
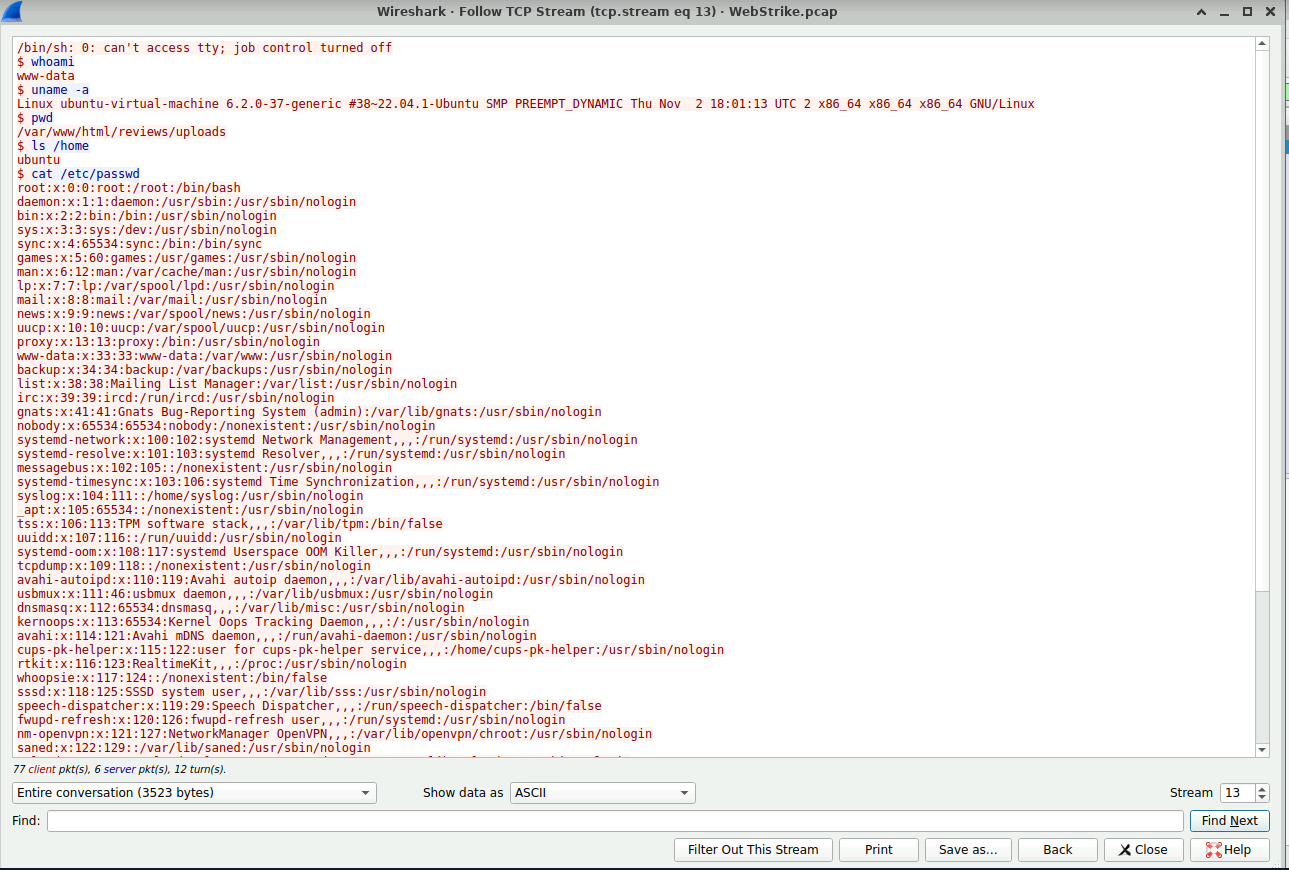
Well, well, WebStrike Lab. Looks like you’ve been…Thunderstuck! See you all in the next one!