PoisonedCredentials Lab
Reviewed PCAP for LLMNR/NBT-NS Poisoning Attack.

Link
Process
I had to look-up what an LLMNR/NBT-NS Poisoning was. So, I consulted the ChatGPT and the MITRE Framework. I include the MITRE here for your perusal. Anyways, on to the Wireshark.

https://attack.mitre.org/techniques/T1557/001/
Okay so the first thing that we had to do was spot a query that was mistype originating from 192.168.232.162. So, let’s set a filter for `ip.src == 192.168.232.162 && (llmnr || nbns || mdns), where it uses our source IP and the potential poisoned protocols. The typo should standout.
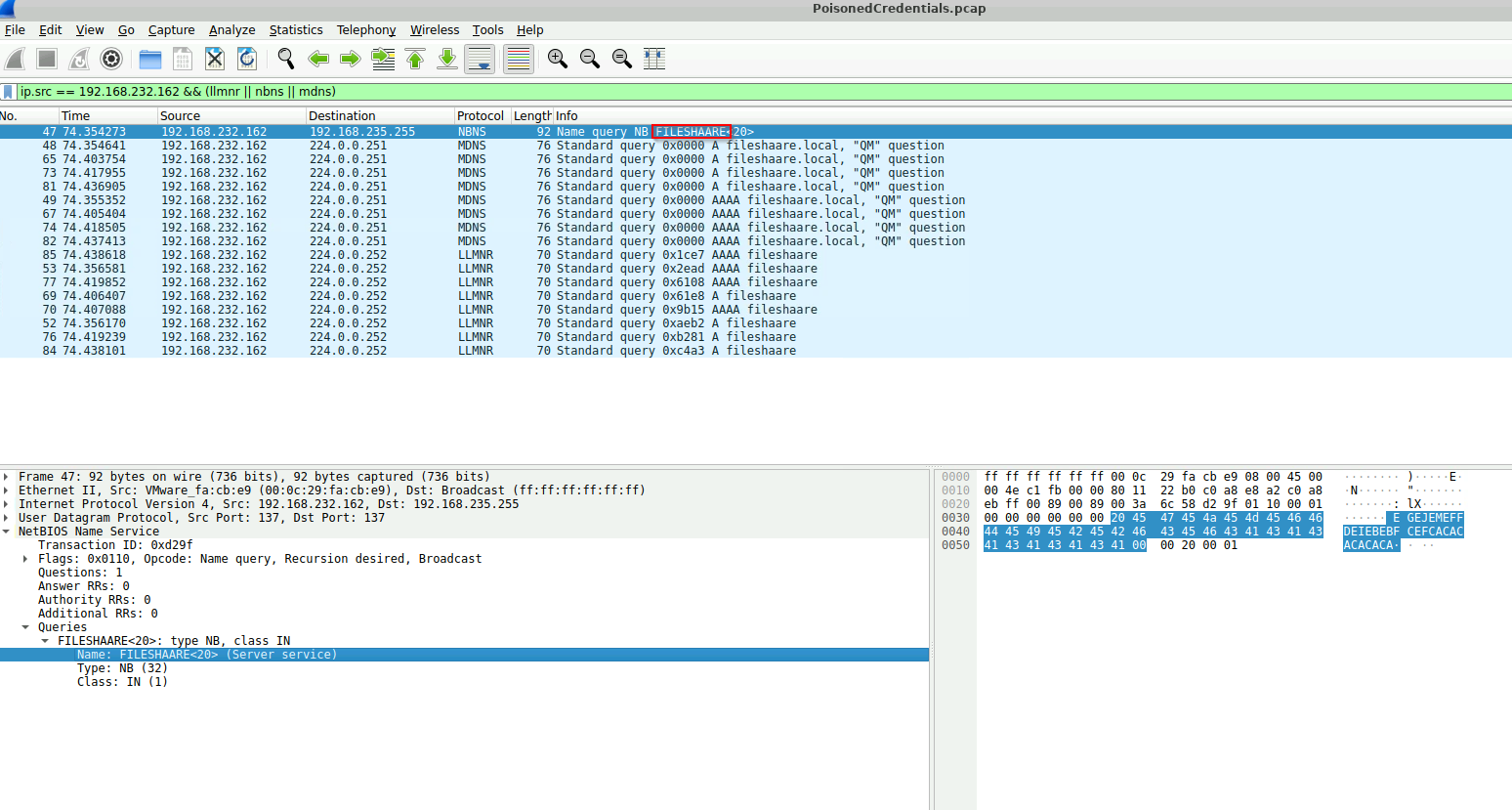
Next thing we have to identify is the rogue machine in the system. So, shortly after the Name query request, we should see the Name query response giving up the rouge IP.
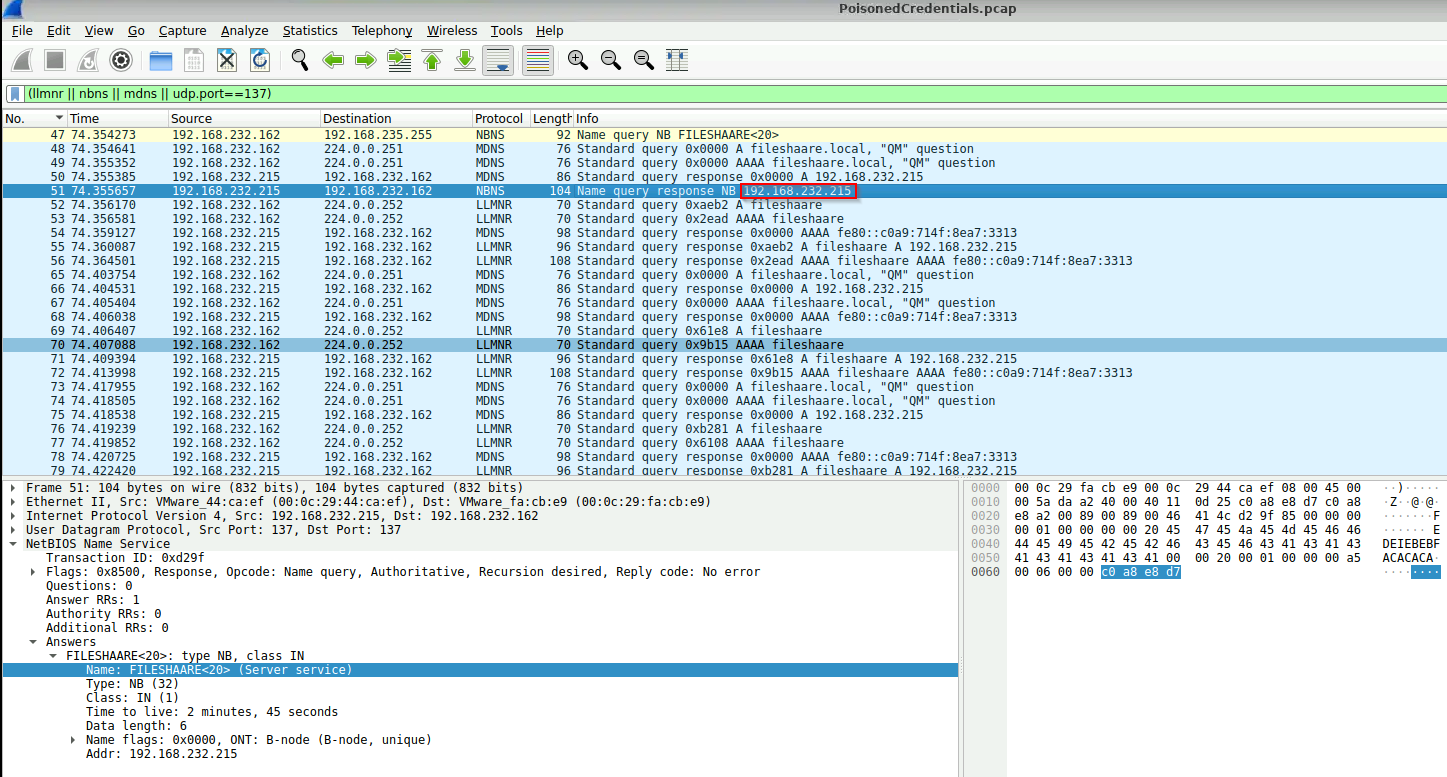
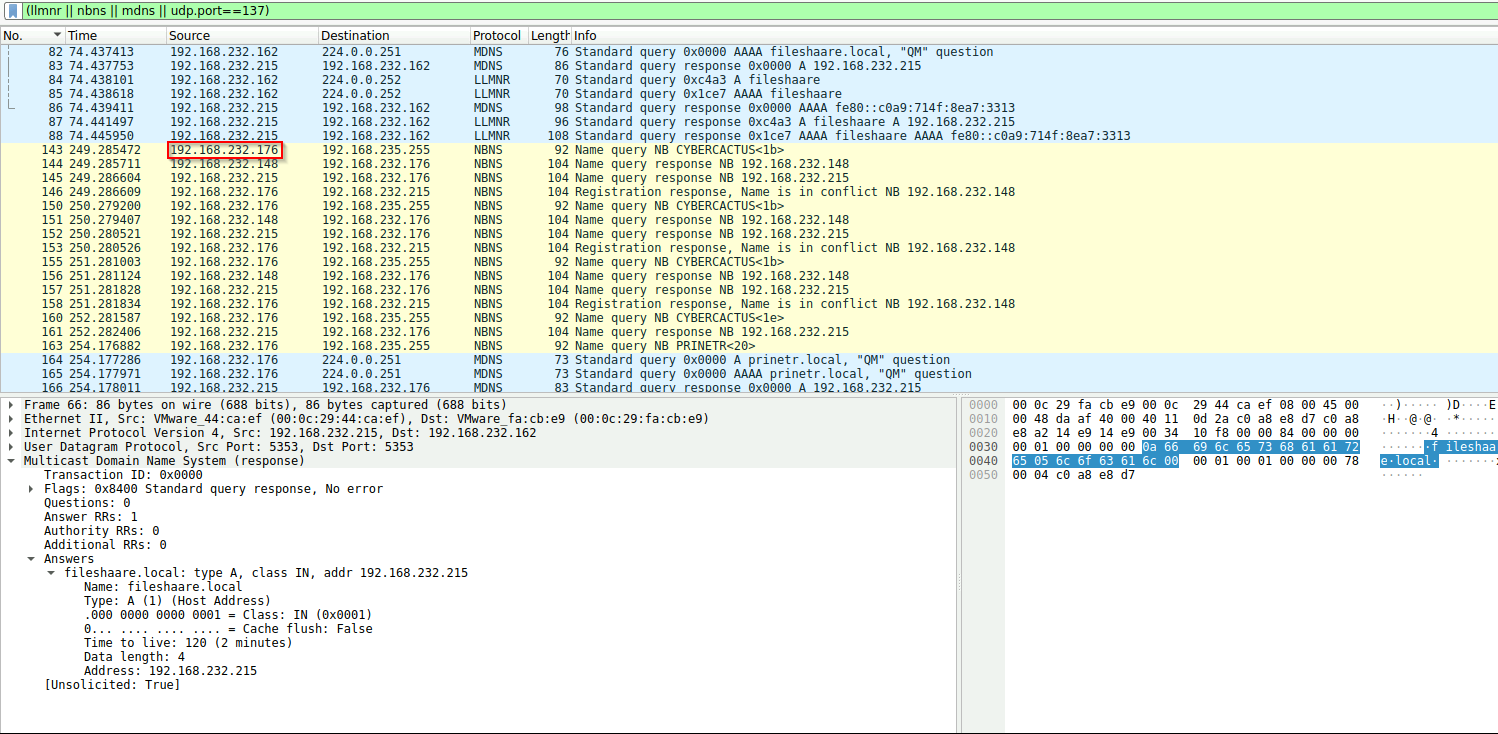
After this, we should probably identify other potentially compromised machines. Look for another IP that the 192.168.232.215 responds to.
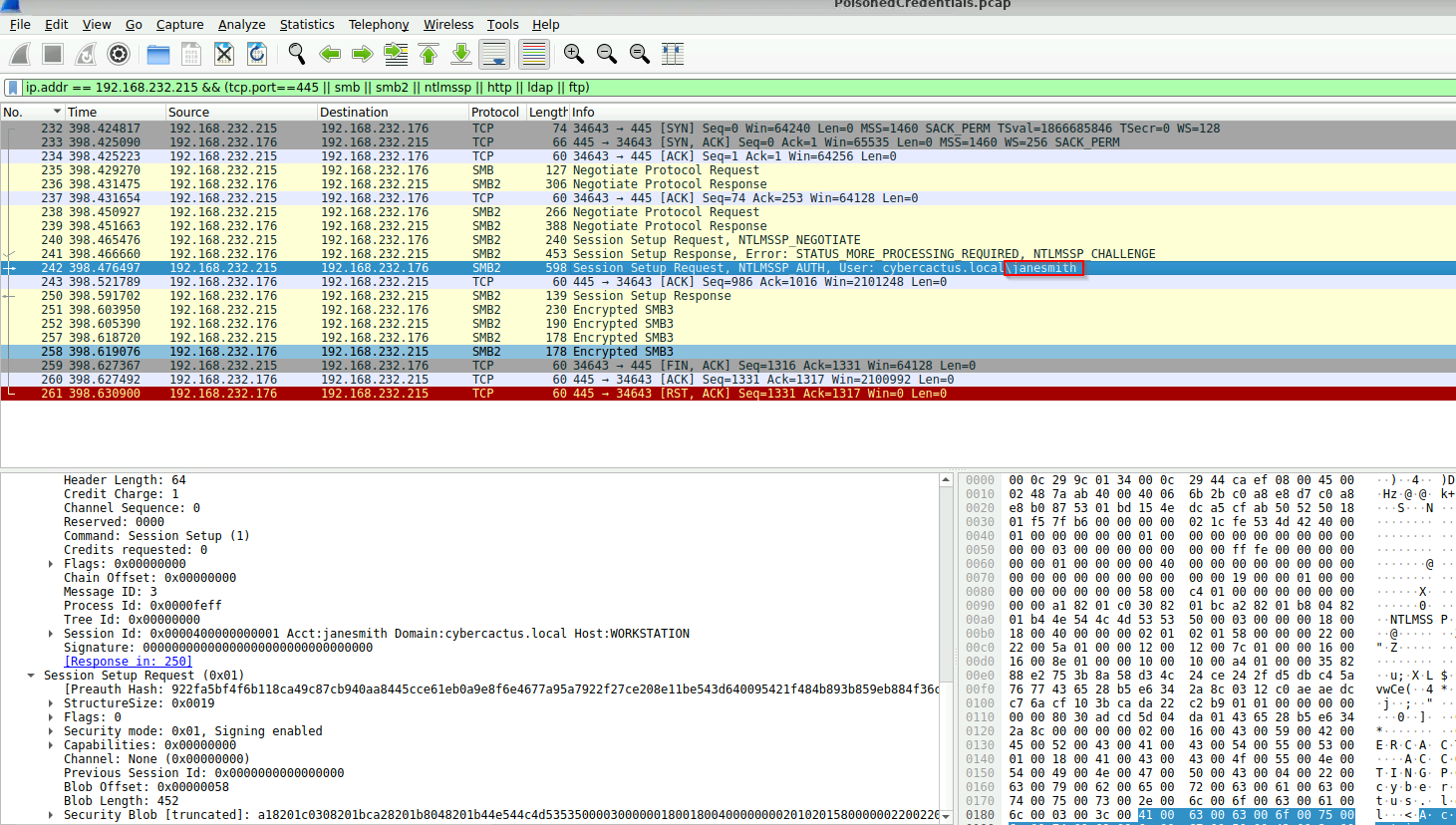
Scrolling through the traffic, if we filter for the rouge IP and smb protocol, we should be able to identify an auth request and get the user name.
Okay, now for this last one, I had to burn all the hints. I struggled. But if we use the ntlm.challenge.target_info filter, there is one request. And if we drill down deep enough into the request, we should come across the NetBIOS computer name.

And with that, another attack bites the dust. See you in the next one!