Oski Lab
Analyzed Virustotal and Any.Run virus reports.

Link
Process
First thing up, let’s get the hash so we can search it online.
┌──(kali㉿kali)-[~/Desktop/oski/temp_extract_dir] └─$ cat hash.txt MD5 Hash: 12c1842c3ccafe7408c23ebf292ee3d9 Use this hash on online threat intel platforms (e.g., VirusTotal, Hybrid Analysis) to complete the lab analysis.
We can then take this hash value and plug it into VirusTotal.
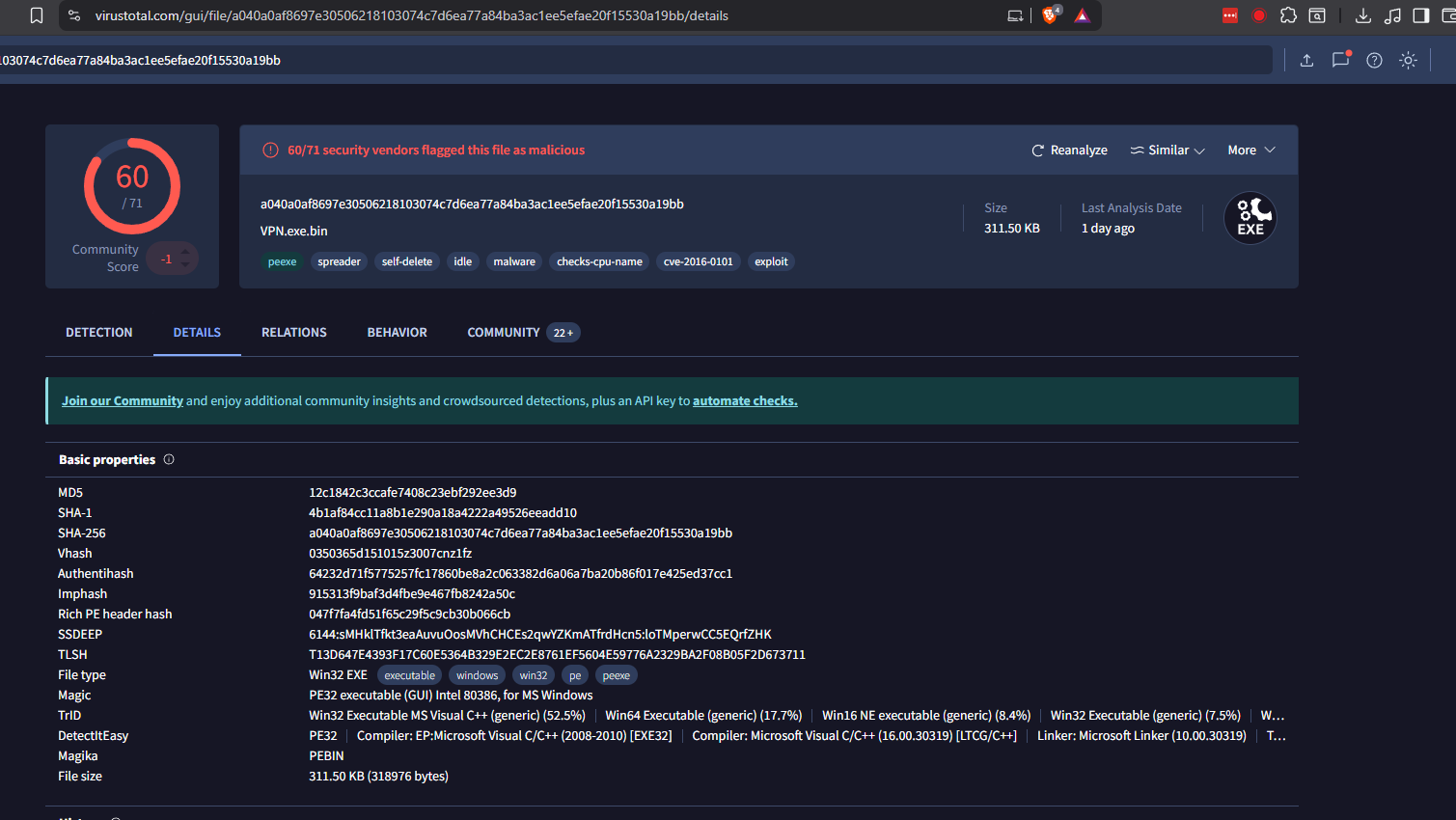
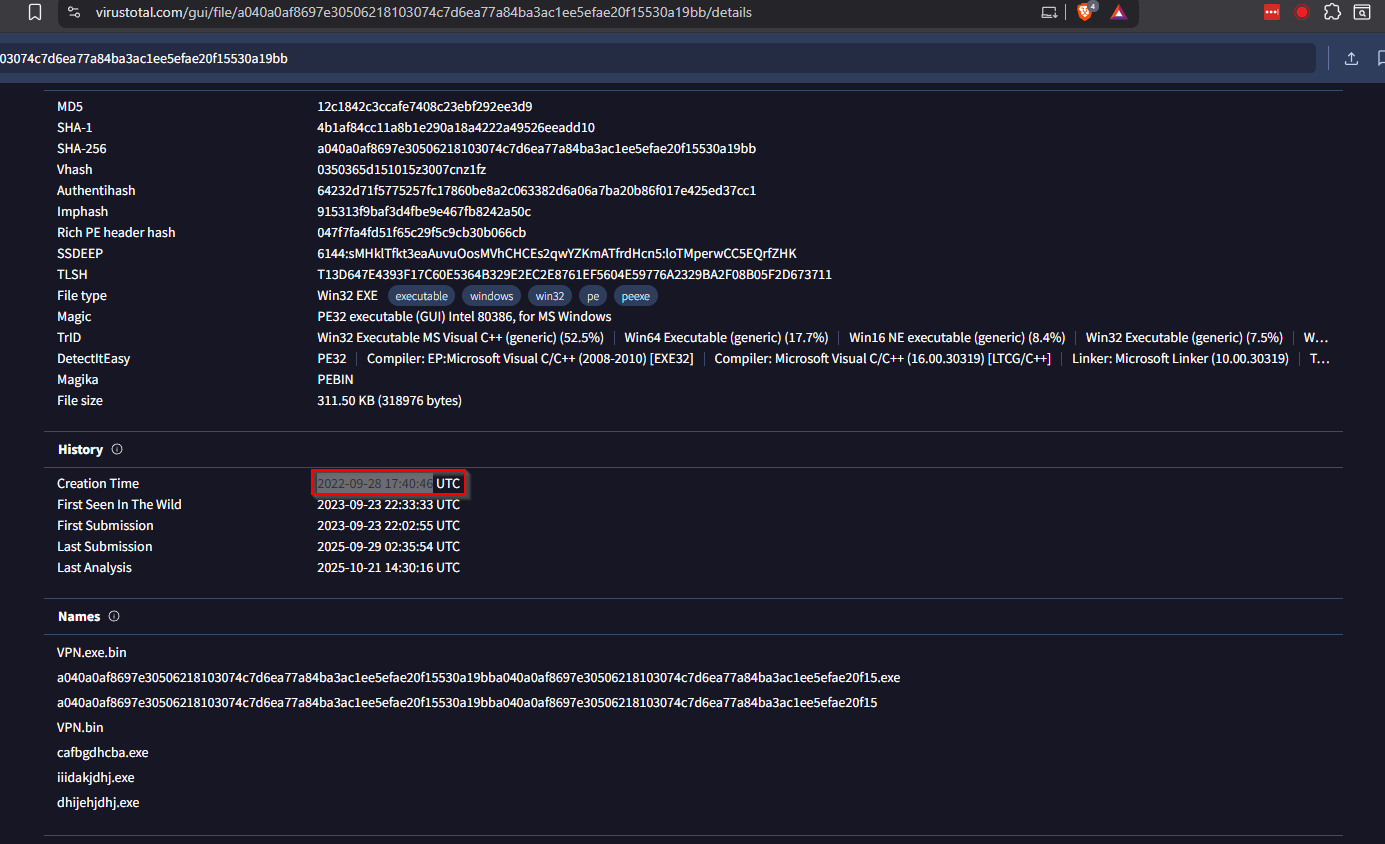
Review the VirusTotal output to find the Creation Time in the History section.
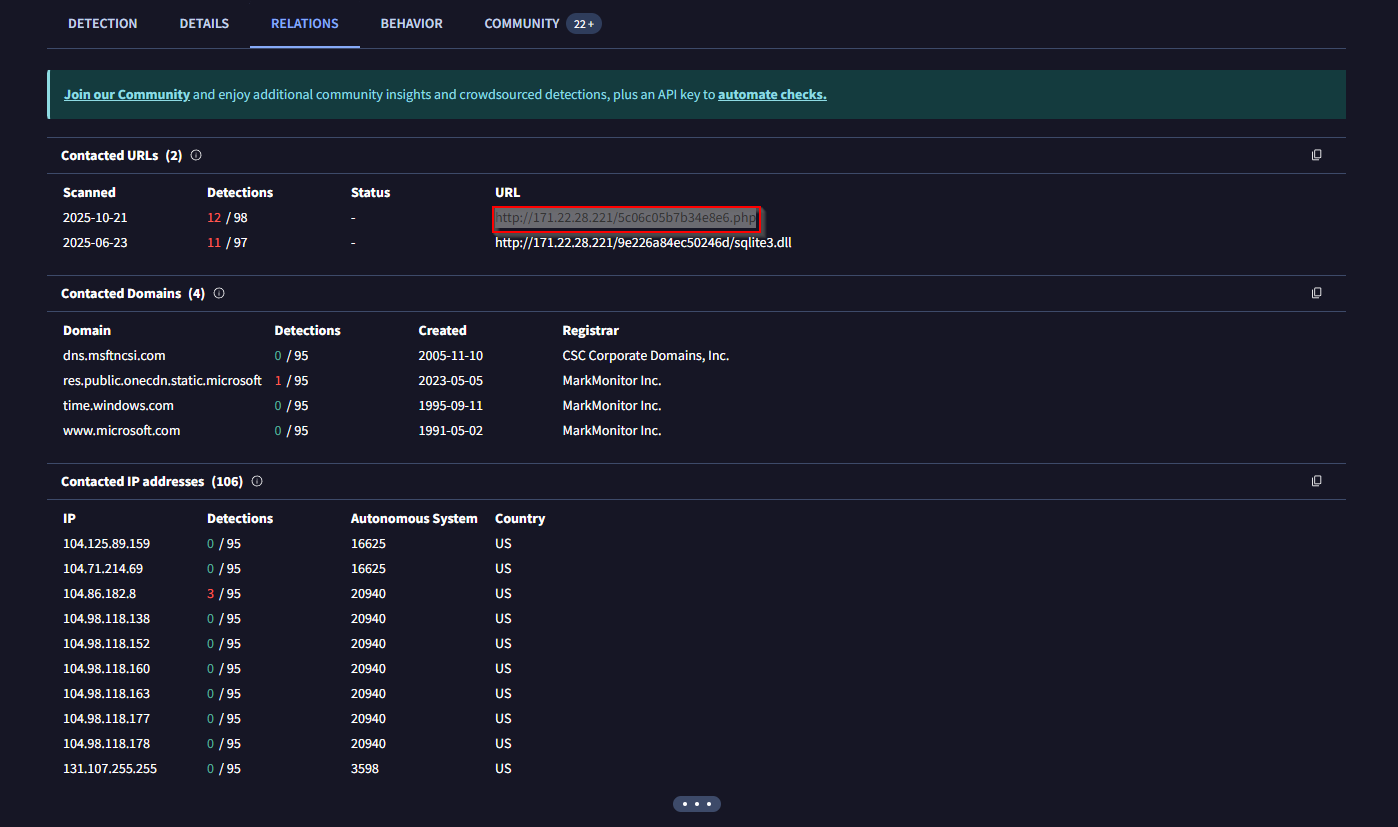
If we review the Contacted URLs, we can the URL of the C2 server.
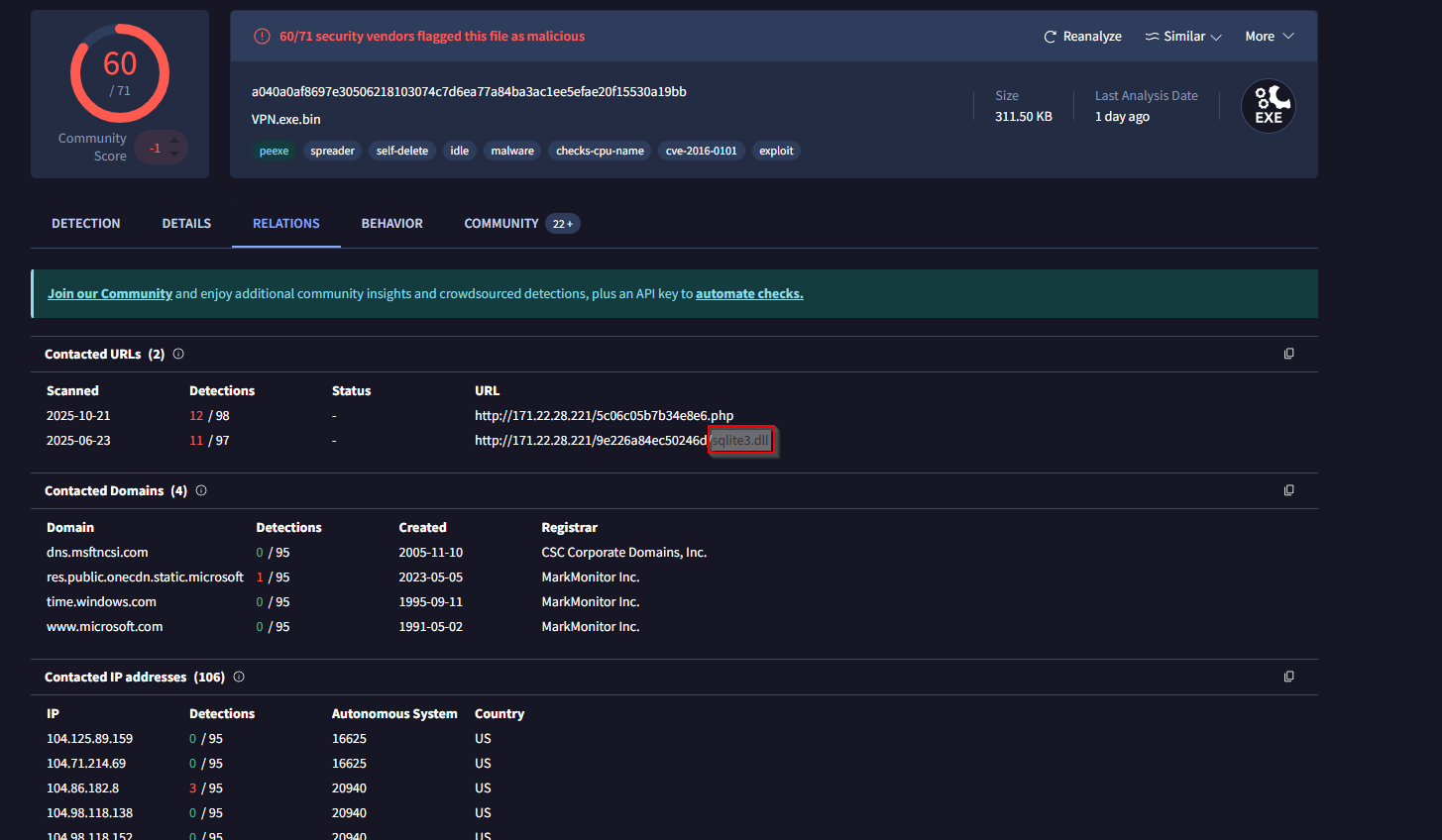
In that same section, we can get the first library that the malware first requested.
Moving on to the any.run report, we can get the RC4 key.
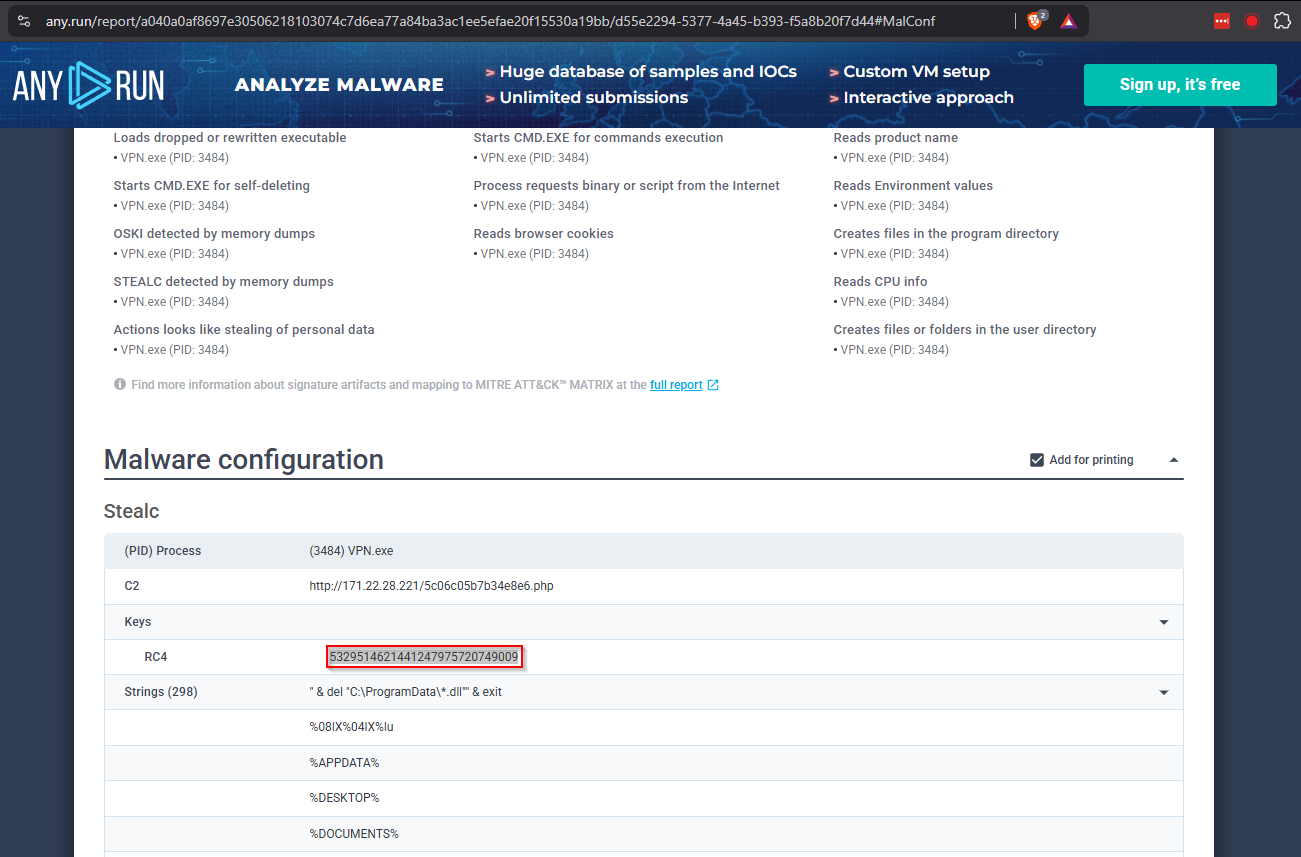
If we review the any.run run, we can get the MITRE framework Technique ID. If we click on the VPN.exe process, it will expose the Technique ID.
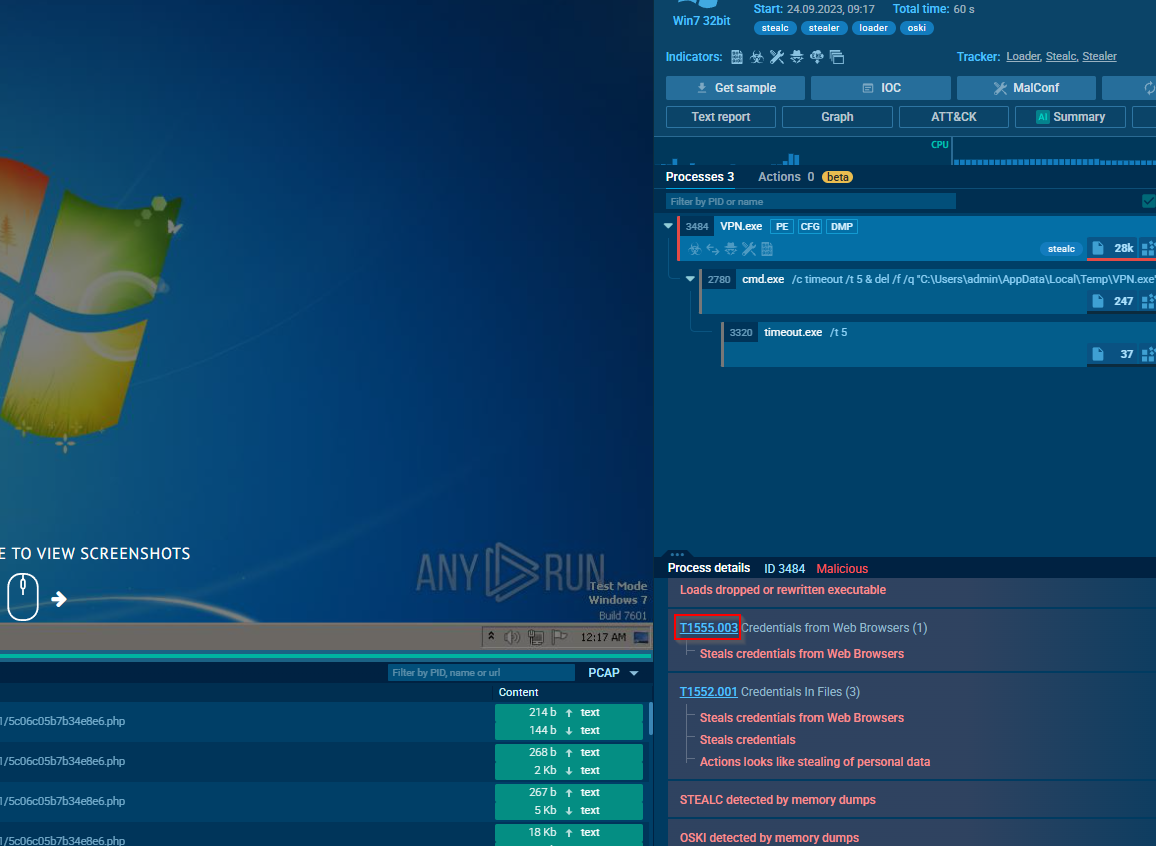
From this same run, you can get the delete command from the cmd command prompt.
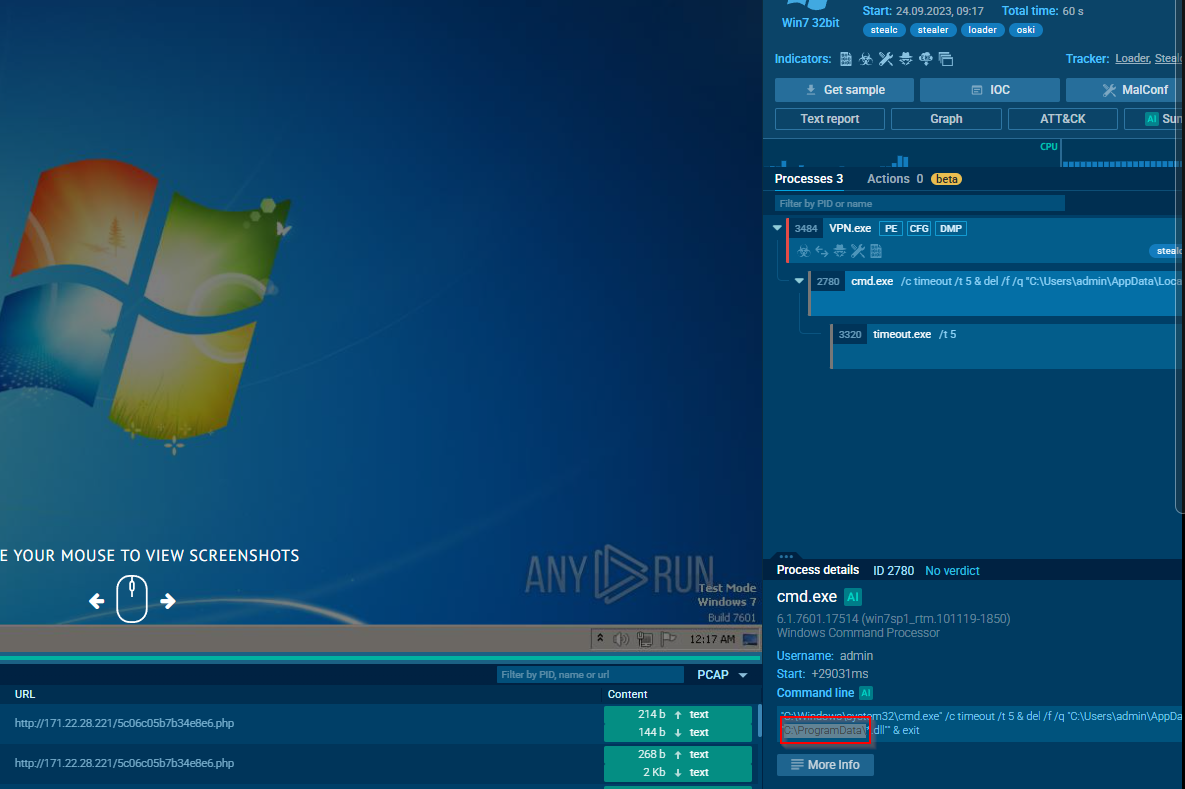
If we get the cmd details, we can get the timeout time value.

With that, we wrapped this one nicely. Hopefully, you enjoyed the read.