Unit42
Reviewed event logs for malware distribution.

Link
Process
It is time for something new. Work on Unit42!
The first action to take is to use EvtxECmd.exe to extract the logs from the .evtx file and export them to csv for easier analysis.
PS C:\Users\win\Downloads\EvtxECmd\EvtxeCmd> .\EvtxECmd.exe -f C:\Users\win\Desktop\unit42\Microsoft-Windows-Sysmon-Operational.evtx --csv C:\Users\win\Downloads\EvtxECmd\EvtxeCmd\ EvtxECmd version 1.5.2.0 Author: Eric Zimmerman (saericzimmerman@gmail.com) https://github.com/EricZimmerman/evtx Command line: -f C:\Users\win\Desktop\unit42\Microsoft-Windows-Sysmon-Operational.evtx --csv C:\Users\win\Downloads\EvtxECmd\EvtxeCmd\ Warning: Administrator privileges not found! CSV output will be saved to C:\Users\win\Downloads\EvtxECmd\EvtxeCmd\20251224150130_EvtxECmd_Output.csv Maps loaded: 453 Processing C:\Users\win\Desktop\unit42\Microsoft-Windows-Sysmon-Operational.evtx... Chunk count: 3, Iterating records... Record # 4 (Event Record Id: 118750): In map for event 26, Property /Event/EventData/Data[@Name="Archived"] not found! Replacing with empty string Record # 27 (Event Record Id: 118773): In map for event 10, Property /Event/EventData/Data[@Name="SourceProcessGuid"] not found! Replacing with empty string Record # 27 (Event Record Id: 118773): In map for event 10, Property /Event/EventData/Data[@Name="TargetProcessGuid"] not found! Replacing with empty string Record # 46 (Event Record Id: 118792): In map for event 26, Property /Event/EventData/Data[@Name="Archived"] not found! Replacing with empty string Event log details Flags: None Chunk count: 3 Stored/Calculated CRC: 9B75E006/9B75E006 Earliest timestamp: 2024-02-14 03:41:26.4441194 Latest timestamp: 2024-02-14 03:43:26.8870662 Total event log records found: 169 Records included: 169 Errors: 0 Events dropped: 0 Metrics (including dropped events) Event ID Count 1 6 2 16 3 1 5 1 7 15 10 1 11 56 12 14 13 19 15 2 17 7 22 3 23 26 26 2 Processed 1 file in 1.8900 seconds
The first step in this process is to identify the number of events with an Event ID 11 in the Event logs.
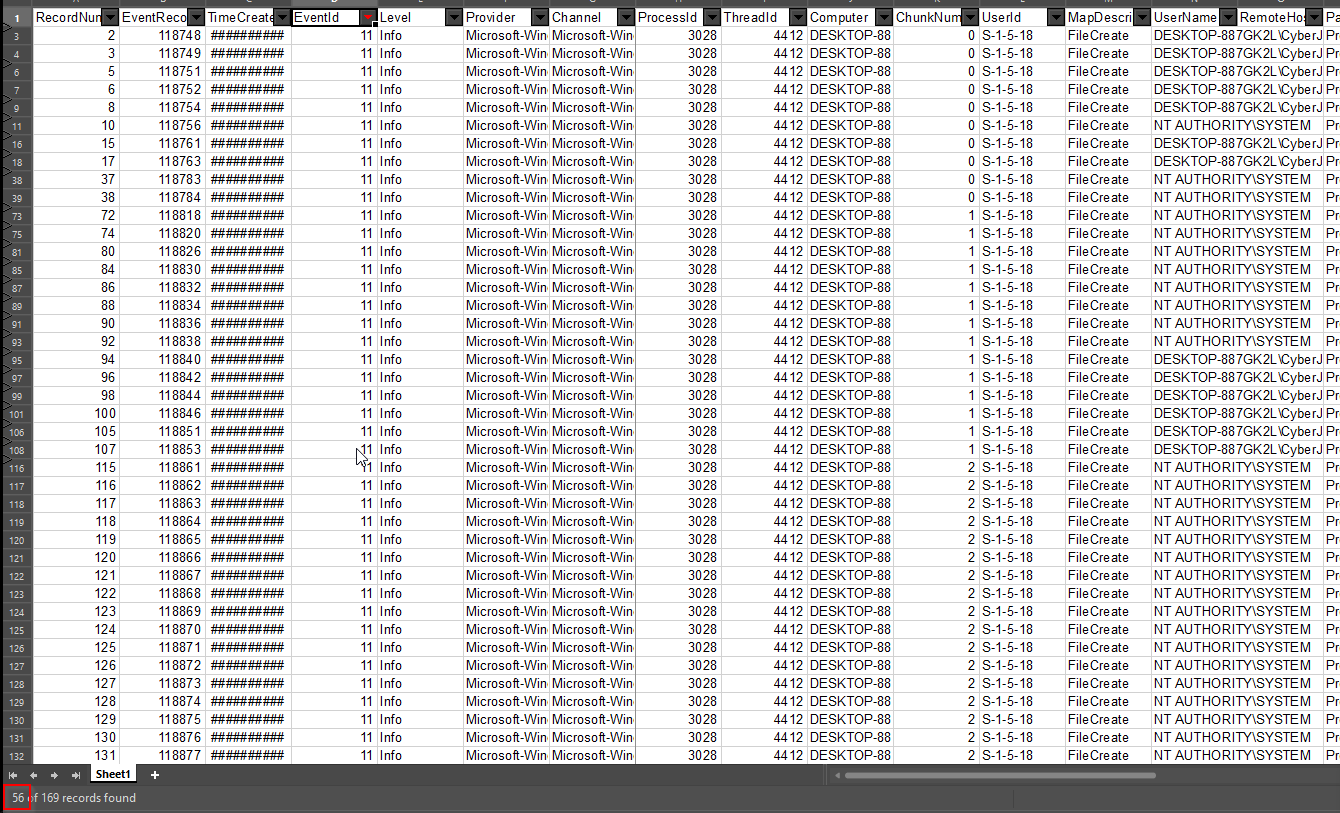
Check the logs for all events where a process is created in memory and search for a executable that stands out as potential malicious.
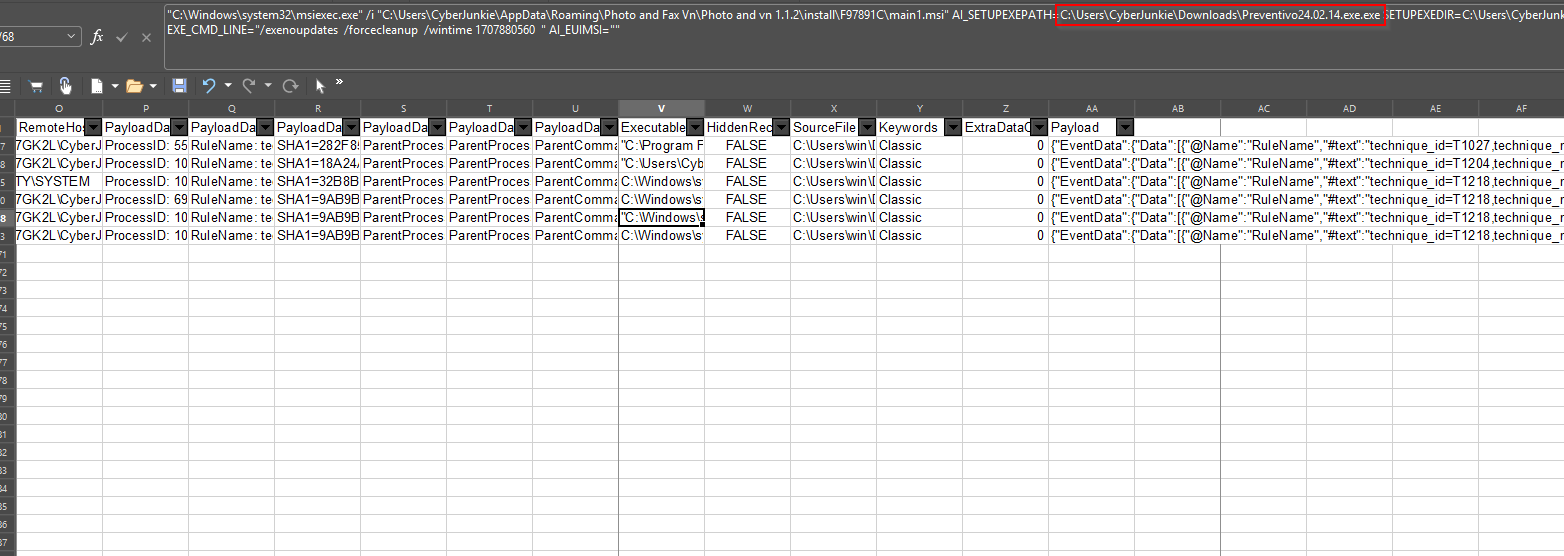
Start by finding the FileCreate event (Event ID 11) that creates the executable. Scroll up from that record and find the DNS record (Event ID 22). Check the EventData to get the domain.
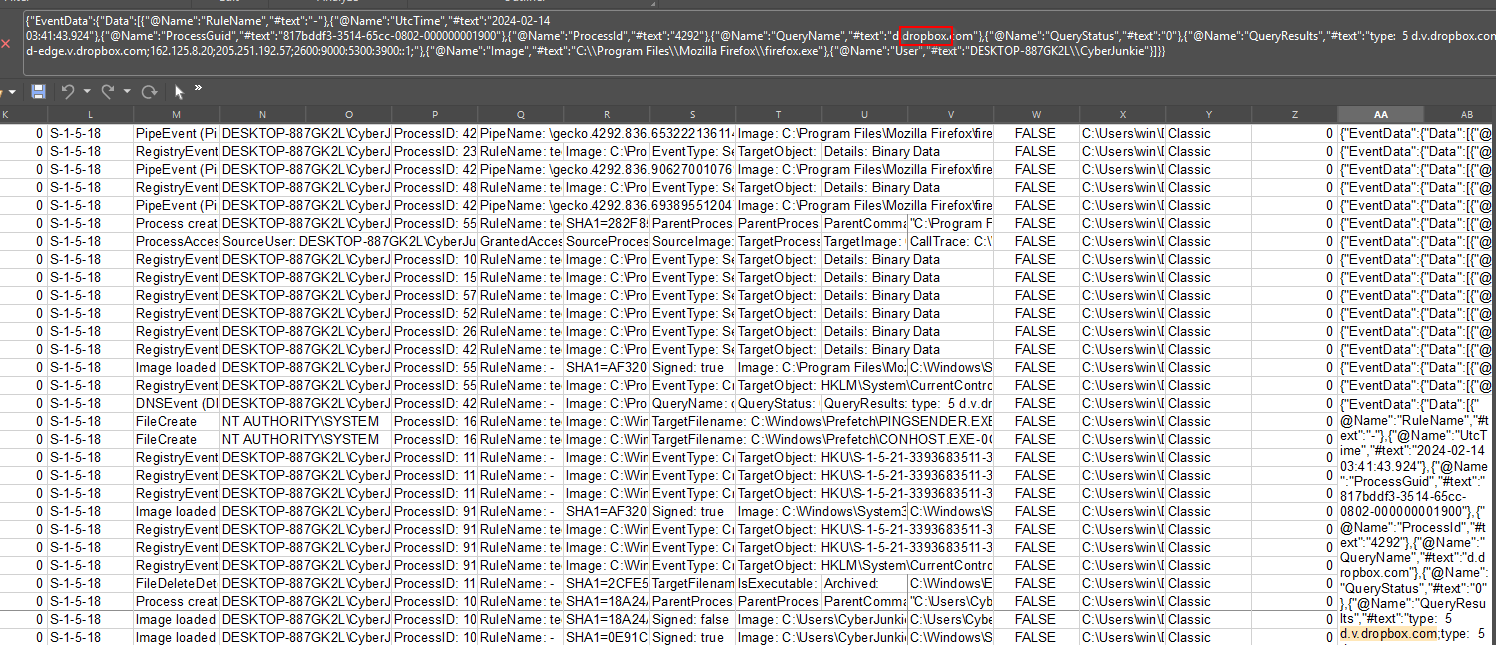
Search for a event with the Event ID 2. Check the EventData for the PDF and not the CreationUtcTime.
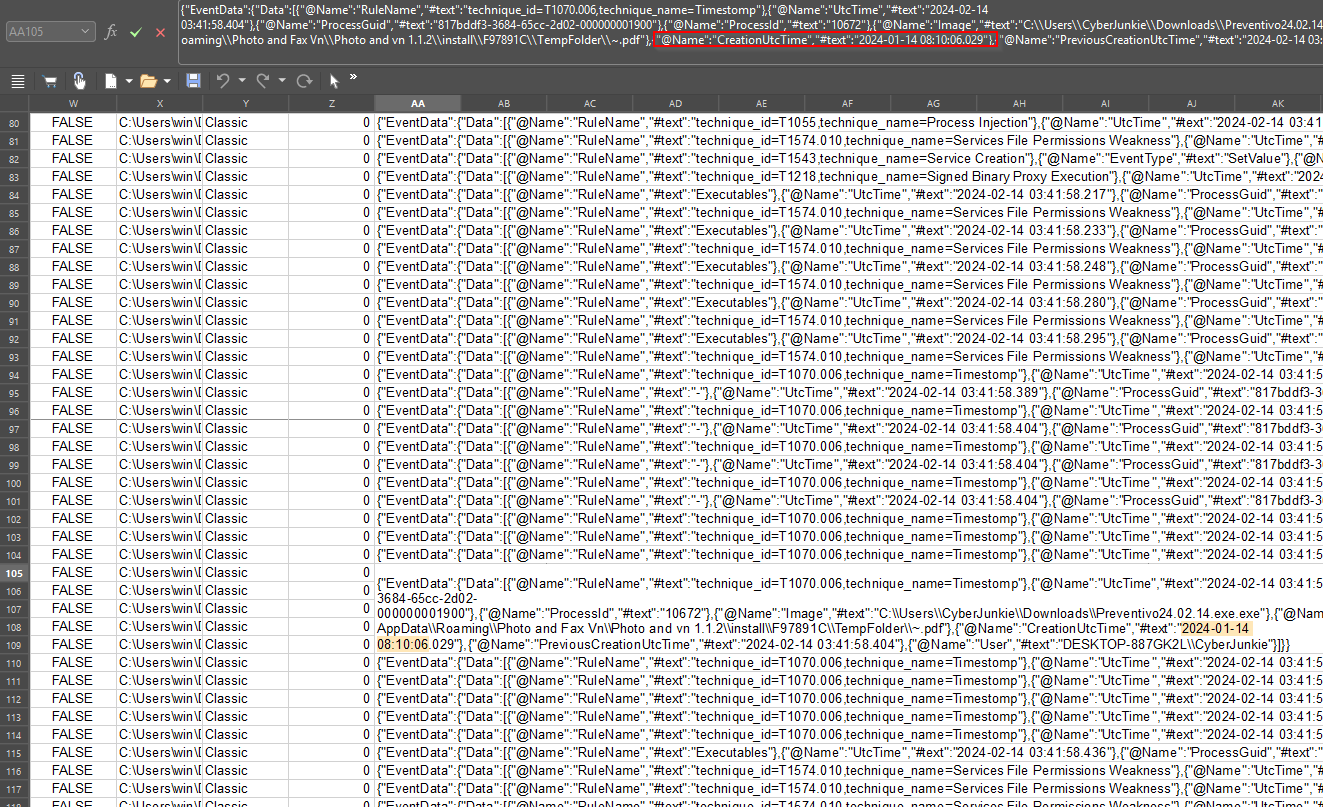
Search for FileCreate and look ing EventData for the once.cmd file.
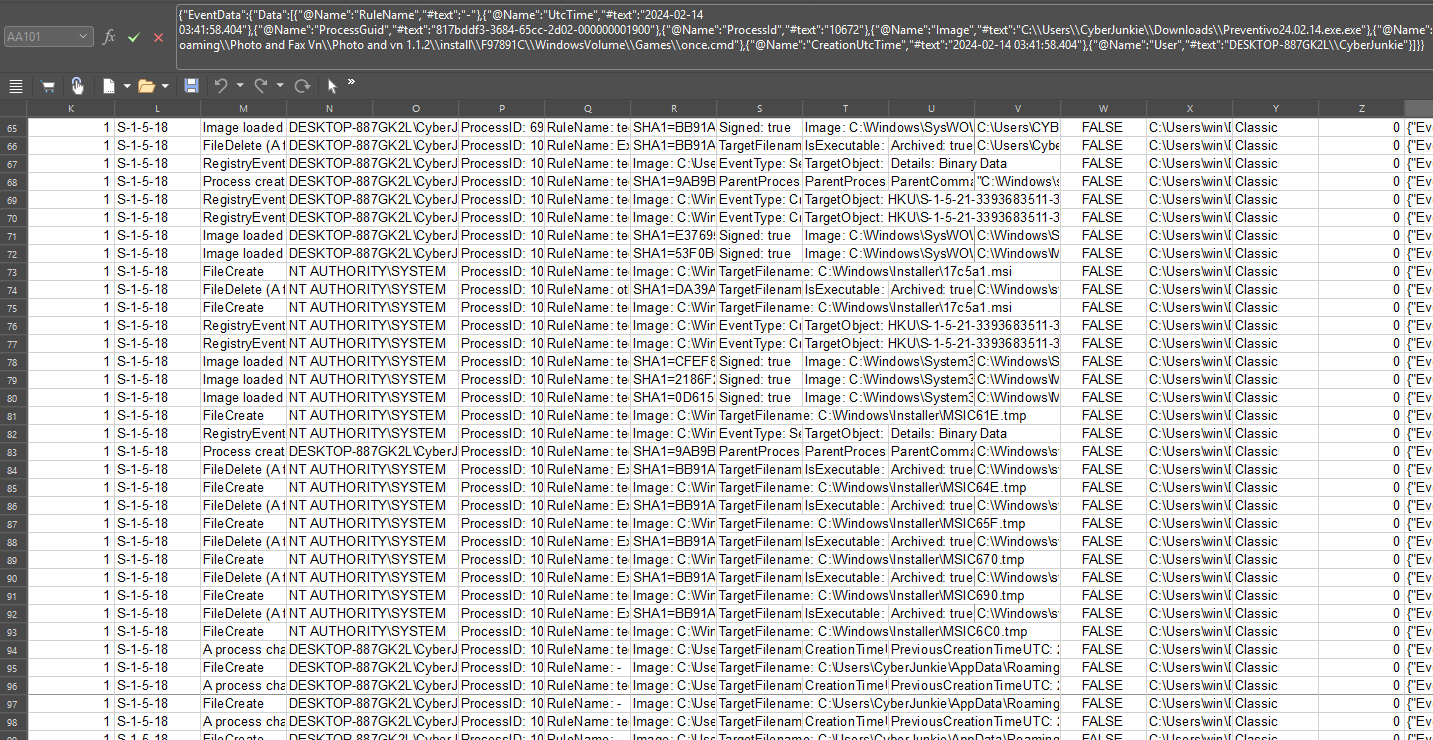
Check for the DNS requests (Event ID 22). Look for the malicious file in the Image column. Get the QueryName.
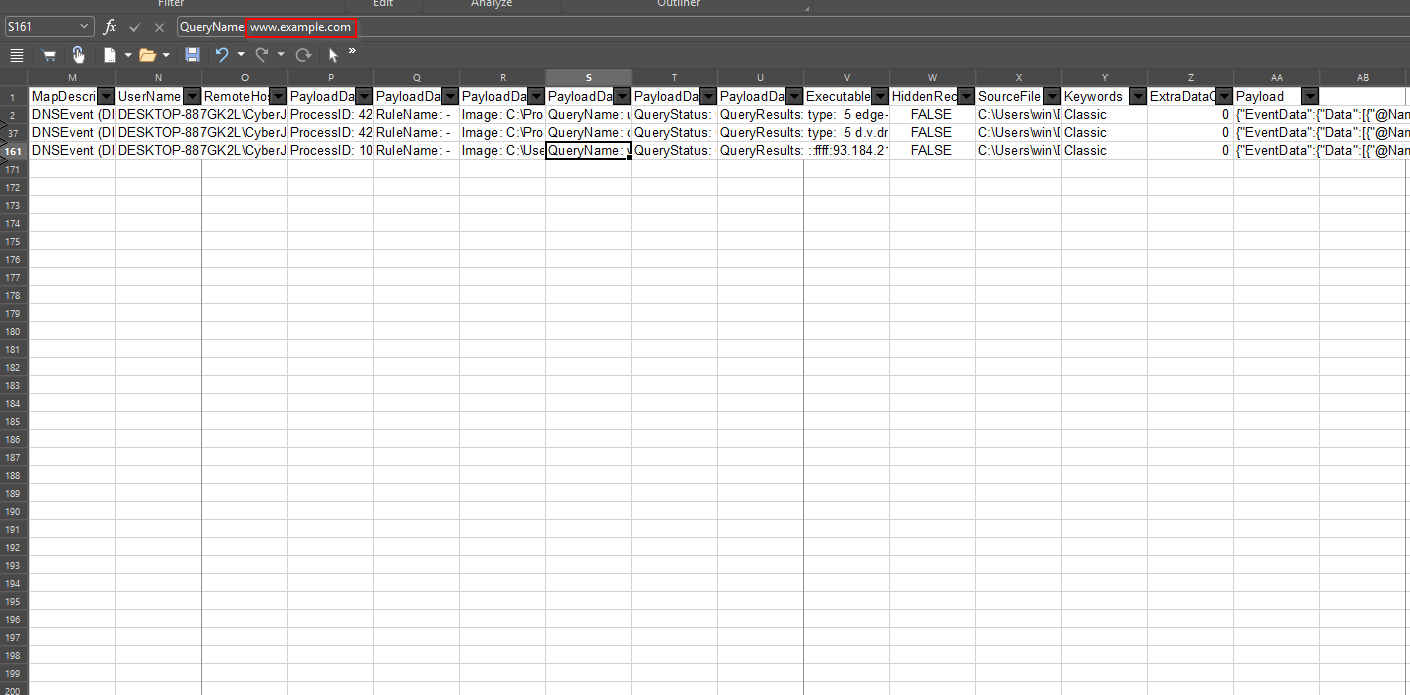
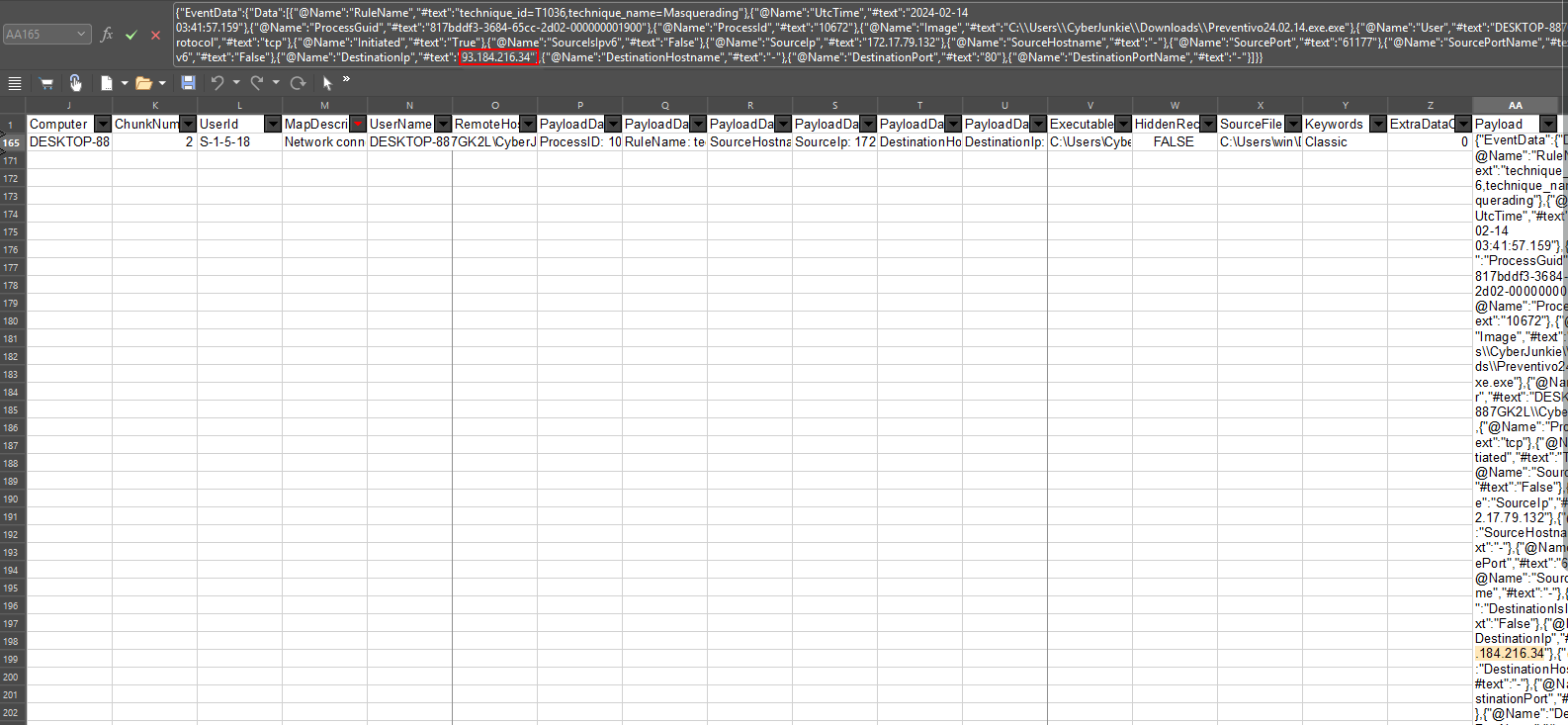
Filter for Network connection using Event ID 3 and check the EventData for the DestinationIP.
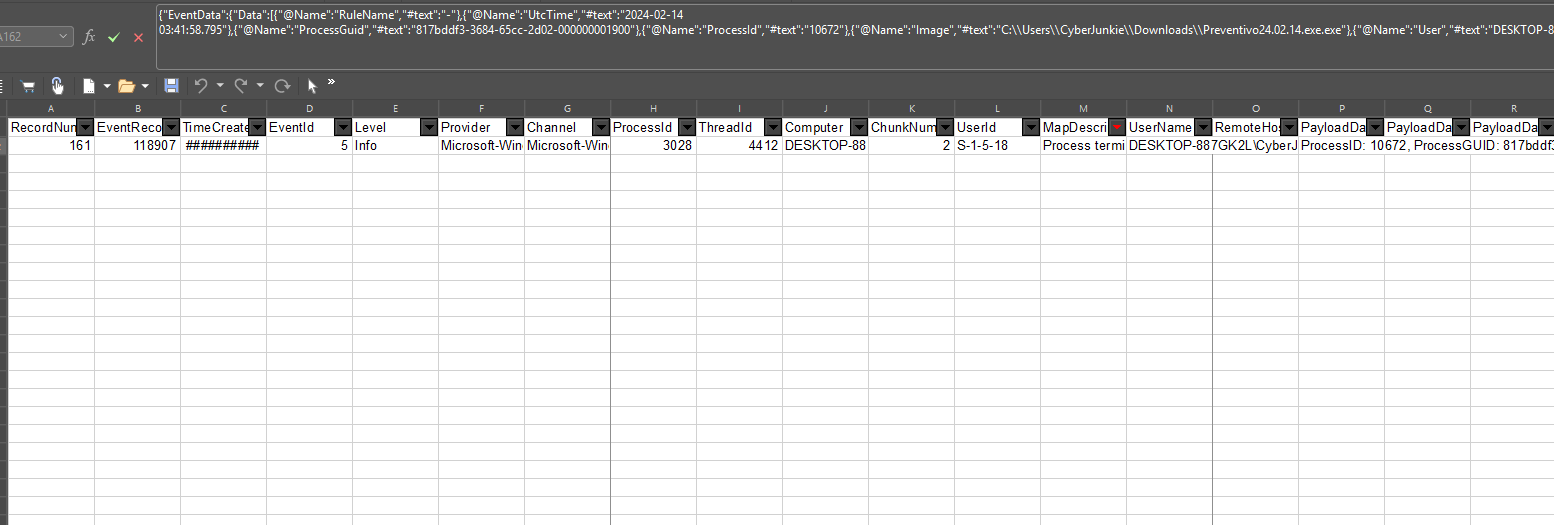
Filter for Process terminated using Event ID 5 and get the time stamp from EventData.
Well, well, what are you going to do? Finish investigating Unit42!